Transparent proxies are becoming a popular way for individuals to protect their online data and maintain their privacy. In this blog post, we’ll explain what transparent proxies are and how they can be used to protect your data and keep your online activity private.
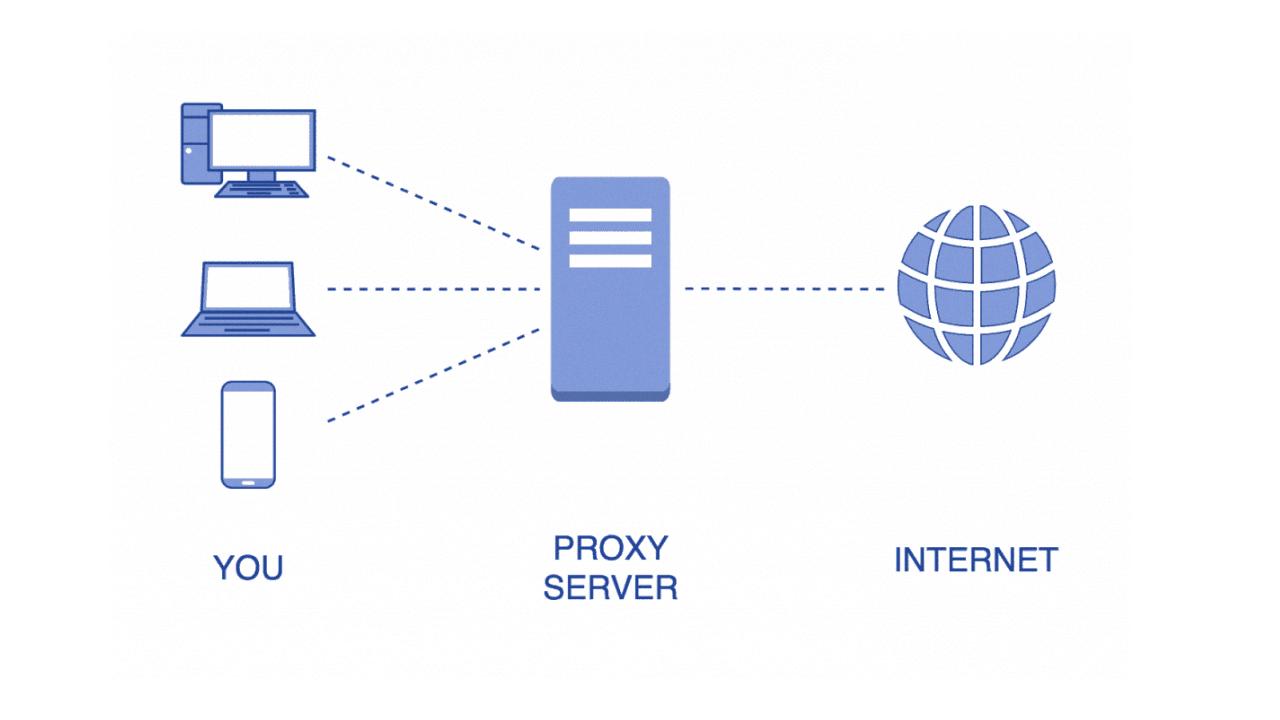
A transparent proxy is a server that sits between your computer and the internet. It intercepts your requests and responses without modifying them, while also hiding your IP address from websites you visit. This allows users to access websites anonymously, without revealing their true identity or location.
Unlike other proxy servers, transparent proxies don’t modify the user’s requests and responses, leaving user data exposed to any potential malicious actors. As a result, users need to be aware of the potential risks of using a transparent proxy.
The most common use of a transparent proxy is for web filtering purposes. Many organizations use transparent proxies to block access to certain websites or content that they deem inappropriate or unsafe for their employees or students. This can be useful in preventing unwanted internet usage in public areas or workplaces, as well as ensuring compliance with organizational policies regarding internet usage.
Another use of transparent proxies is in network security scenarios where an organization wants to monitor all outgoing traffic from its network. Transparent proxies can be used in this situation as they allow an organization to inspect all outbound traffic before it leaves the network and take appropriate action if necessary. They can also help detect malicious activity on the network by logging any suspicious activity that passes through the proxy server.
Overall, while transparent proxies have some useful applications, users should be aware of the potential risks associated with using them. While they offer anonymity and privacy benefits, there is still a risk that user data could be compromised without users’ knowledge or consent if not properly secured against malicious actors.
The Benefits of Using a Transparent Proxy
The answer to whether a transparent proxy is good depends on the context. In some cases, they can provide benefits such as increased security and improved performance. For example, transparent proxies can be used to filter out malicious traffic or to reduce latency in a network by caching content closer to the user. On the other hand, they can also be used for malicious purposes like monitoring and intercepting traffic without the user’s knowledge or consent. Ultimately, it’s important to evaluate whether the benefits of using a transparent proxy outweigh any potential risks before implementing one.
Is a VPN a Transparent Proxy?
No, a VPN is not a transparent proxy. A transparent proxy is a server that acts as an intermediary between the user and the Internet, directing traffic from the user’s computer to its own server before sending it on to its destination. This type of proxy does not encrypt traffic or require authentication, so it does not provide any of the privacy benefits associated with a VPN. Additionally, a transparent proxy doesn’t hide your IP address—it merely forwards it from one point to another. A VPN, on the other hand, provides data encryption and authentication while also hiding your IP address.
Difference Between Transparent and Non-Transparent Proxies
The primary difference between transparent and non-transparent proxies is that the former does not modify requests or responses, while the latter does. Transparent proxies act as a gateway to the internet, redirecting traffic without altering it, while non-transparent proxies alter the content of requests and responses in order to provide additional services.
Transparent proxies are usually used for caching web pages and providing enhanced security, while non-transparent proxies are used to enforce access control policies, provide additional services such as content filtering, or add extra features such as compression. They can also be used for bypassing firewalls or geo-restrictions, allowing users to access websites that would otherwise be blocked in their region.
Additionally, transparent proxies can be configured on a user’s computer or router without requiring any changes on the client side. Non-transparent proxies require additional client-side setup in order to work properly. This means that transparent proxies are often easier to set up and more suitable for home networks than non-transparent ones.
Does a Transparent Proxy Hide Your IP Address?
No, a transparent proxy does not hide your IP address. Instead, it acts as a middleman between you and the destination server. It forwards requests from you to the destination server and then sends the response back to you. All of your requests are visible to the proxy server and it is able to collect data about your activities, including your IP address. Therefore, while using a transparent proxy may provide some additional security benefits, it will not hide your IP address.
The Purpose of a Transparent Proxy
A transparent proxy is a type of proxy server that is used to filter out unwanted content while still allowing users to access the internet. It works by intercepting web requests, filtering those requests based on certain criteria, and then either forwarding or denying the request. This can be used to block access to certain websites, prevent users from downloading malicious files, or even just hide a user’s identity and location from websites they visit. Transparent proxies are often used in larger organizations where network administrators need a way to control what content users are able to access.
The Benefits of Using a Proxy Over a VPN
Proxy is better than VPN because it provides a greater level of anonymity and privacy. Unlike VPN, which only encrypts the data traffic between a client and server, proxies also hide the IP address of the client in order to protect their identity. This means that the proxy server can act as an intermediary between the client and other websites or services, allowing them to remain anonymous while they browse or access those sites. Furthermore, proxies are often faster than VPNs because they don’t require any software to be installed on the client’s device. They are also simpler to use, as all you need to do is configure your browser settings to use a proxy server. Finally, proxies can be used for both personal and business purposes, allowing you to securely access restricted content and bypass geo-blocking restrictions.
Source: outreachbee.com
The Benefits of Using Transparent SSL Proxy
A transparent SSL proxy is a type of network security tool that allows for secure, encrypted connections between a client and server. It works by encrypting and decrypting data between the two endpoints, while also providing the server with a certificate to enable it to open a secure (SSL) or unsecure (HTTP) connection to the web server. This helps protect data from being intercepted, tampered with or sniffed out by malicious actors. The transparent SSL proxy is also known as an SSL forward proxy or just an SSL proxy.
Can a Proxy Be Used to Track a Person?
Yes, you can be tracked with a proxy. Although a proxy can help you maintain some level of anonymity online, this does not mean that your data is completely untraceable. Without encryption, websites can still see what you do online as the traffic passes through the proxy server. However, they will not be able to connect that activity to your real IP address, which makes it difficult for them to track you.
Does a Proxy Hide Your Browsing History?
Yes, a proxy server can help hide your browsing history from your ISP. When you connect to a proxy server, it will act as a middleman between you and the websites you visit. The proxy will hide your IP address and mask your activities, so your ISP won’t be able to view or track what sites you are visiting. Additionally, using a proxy can speed up your browsing experience by caching webpages for faster loading times.
Can a Proxy Server Effectively Hide Your Identity?
Yes, a proxy server can really hide your identity online. When you connect to the internet through a proxy server, your computer’s IP address is replaced with the IP address of the proxy server. This means that websites and other services will see the IP address of the proxy server instead of your own IP address, which makes it much harder to trace any online activity back to you. Additionally, some proxy servers even encrypt the data sent between your computer and the proxy server, so that it can’t be intercepted or read by anyone else. By using a proxy server, you can effectively mask your identity and remain anonymous while browsing the internet.
Conclusion
In conclusion, transparent proxies can be used for both beneficial and malicious purposes. They provide users with the ability to access restricted websites anonymously, but they also put users’ data at risk of being compromised by hackers and other malicious users. It is important to understand the risks associated with transparent proxies before using them and to use a VPN instead if you want to ensure your online activities remain private.