Role-based access control (RBAC) and attribute-based access control (ABAC) are two of the most important mechanisms for implementing access control in an organization. They both allow you to protect sensitive data from unauthorized access, but they differ in terms of how they determine who can access what.
RBAC is a system that grants or denies access based on the requesting user’s role within a company. This means that users are assigned specific roles that determine what level of access they have to certain resources and information. For example, an employee with the role of “manager” might have more privileges than an employee with the role of “intern”. RBAC takes time to set up because it requires defining all the roles and privileges associated with them, but once it is configured it can be very efficient as long as the roles remain constant.
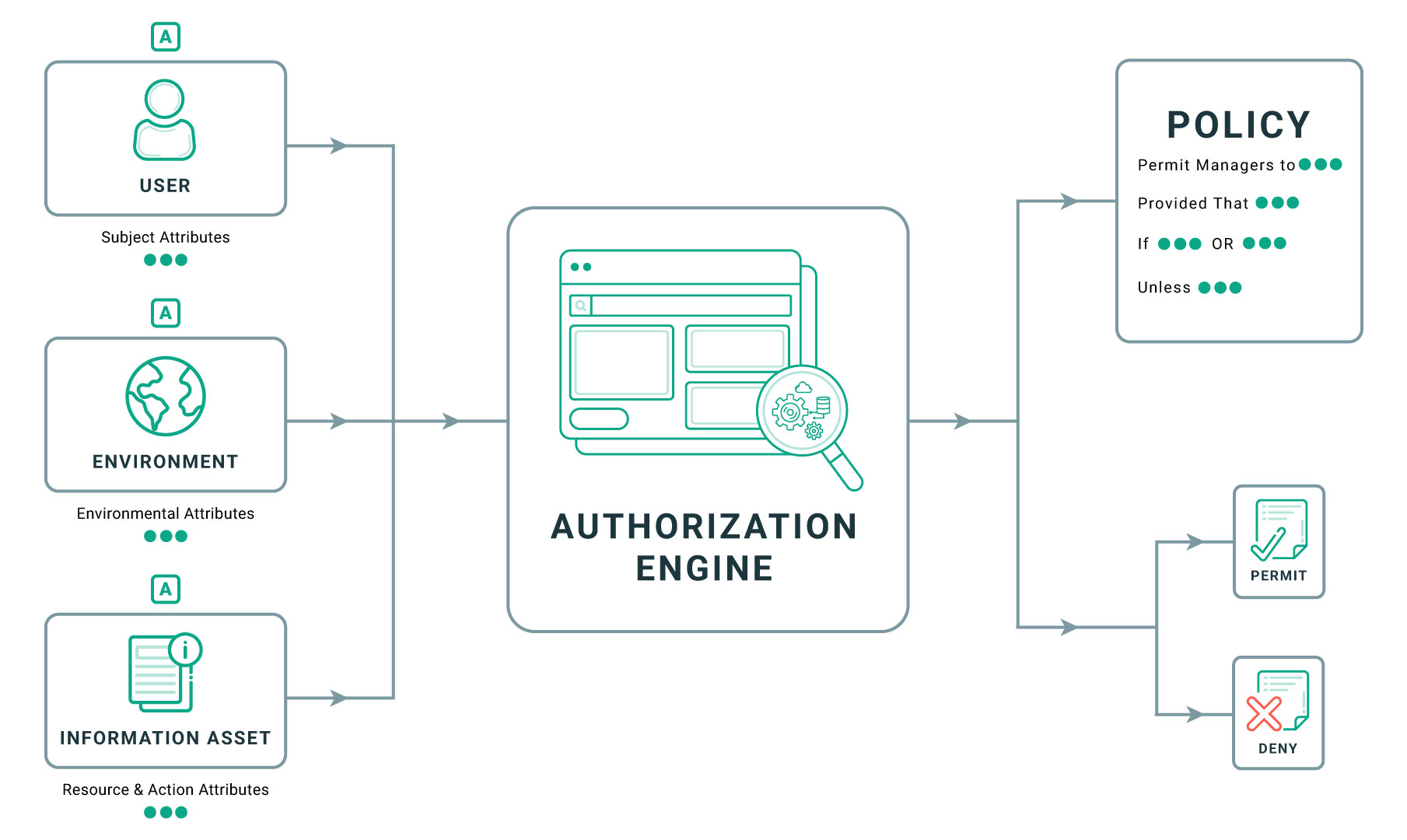
ABAC, on the other hand, grants or denies access based on attributes associated with each user, resource, and environment involved during sign-on. This means that each individual has their own unique set of attributes that determine their level of privilege and which resources they can access. ABAC is much more flexible than RBAC since it doesn’t require pre-defining roles or privileges; instead, it uses rules to determine which users should be granted or denied access based on their attributes. For example, a rule might state that only users with certain job titles should be able to view certain documents.
Both RBAC and ABAC offer effective security solutions for organizations looking to protect their data from unauthorized use or exfiltration. However, depending on your organization’s structure and needs, one may be better suited than the other. Organizations with a simple structure and few roles may find that RBAC is a better choice while those who need more flexibility may prefer ABAC.
What Are RBAC And ABAC?
Role-based access control (RBAC) is a method of controlling access to resources based on the roles of individual users within an organization. RBAC assigns permissions to users based on their job function, allowing them to access only the information and tools that are appropriate for their job. This method of access control can be used in both physical and digital resources.
Attribute-based access control (ABAC) is a more flexible approach to access control than RBAC. ABAC grants or denies access to a resource based on the user’s attributes such as location, time, device type, etc. This approach allows for greater granularity in defining who can access what resources and when. ABAC also enables organizations to quickly adapt their security policies as needed, making it especially useful for dynamic environments where user roles and tasks may change frequently.
Comparing ABAC and RBAC: Which is Better?
ABAC (Attribute Based Access Control) is a more modern approach to access control than RBAC (Role Based Access Control). ABAC allows for more fine-grained control over access than RBAC, as it takes into account a variety of attributes such as user roles, group membership, time of day, and other contextual information when deciding which users have access to which resources. This makes ABAC much more dynamic and flexible than RBAC, as the rules can be easily updated or changed if needed. ABAC also allows for more granular security settings and is better suited for today’s increasingly complex IT environments. With ABAC, organizations can create rules that are tailored to their specific needs rather than using generic rules that may not always fit the situation. Additionally, ABAC is faster to set up and configure than RBAC since all the necessary attributes can be quickly defined with automated processes. All in all, ABAC is a better option for organizations looking for an efficient and secure access control system.
Comparing the Security of RBAC and ABAC
Both RBAC (role-based access control) and ABAC (attribute-based access control) are approaches to identity and access management that can provide secure access to resources. Both models involve assigning permissions to users based on certain criteria, but the difference is in the type of criteria used. RBAC assigns permissions based on static roles within an organization, whereas ABAC takes into account other dynamic factors such as time, location, or device type. While both models can be effective for security purposes, ABAC generally provides more granular and detailed control over user access than RBAC does. As such, it may be more suitable for organizations with complex structures or dynamic environments that require a higher level of security.
Comparing RBAC, PBAC, and ABAC
RBAC (Role-Based Access Control) is a type of access control system that grants access to resources based on the user’s role within an organization. It is typically used for authorization and authentication, meaning it determines which users have access to which parts of the system. This type of access control is often implemented by assigning each user a specific role or set of roles that determine what they can do and view in the system.
PBAC (Policy-Based Access Control) is a type of access control system that grants access to resources based on policies and rules created by an administrator. These policies are generally determined by an organization’s security requirements and are enforced when a user attempts to access a resource or service. PBAC allows administrators to define complex rules for granting or denying access to resources, allowing for greater flexibility and control over who can do what.
ABAC (Attribute-Based Access Control) is a type of access control system that grants access to resources based on attributes associated with the user, resource, and environment involved during sign-on. This type of access control works by evaluating the user’s credentials as well as other relevant attributes such as time and location before allowing them to gain access to the requested resource. ABAC provides more granular and fine-grained control over who can gain access to what, allowing organizations greater flexibility in controlling who has access to their systems.
Types of Access Control
Discretionary Access Control (DAC) is a system that grants users access to objects based on their individual user identity. It allows the owner of an object to decide who has access to it and what type of access they have. DAC systems are used in networks, applications, and operating systems to control access rights.
Role-Based Access Control (RBAC) is an access control system that assigns users specific roles that determine which resources they can access. RBAC systems allow administrators to quickly assign and change user permissions based on the user’s role within the organization. This makes it easier for organizations to manage large numbers of users with different levels of access privileges.
Attribute-Based Access Control (ABAC) is an authorization system that allows administrators to set user permissions based on attributes such as age, location, job title, or any other relevant information about a user or group of users. ABAC systems use policies that specify which resources can be accessed by which users or groups for reasons such as compliance with data privacy laws or security requirements.
Example of Attribute-Based Access Control (ABAC)
Attribute-Based Access Control (ABAC) is an access control model that uses attributes, or descriptors, to define the access rights of a user. ABAC is an important security feature in enterprise networks and helps to ensure only authorized users are able to access restricted resources.
An example of ABAC would be allowing only users who have certain attributes like type=employee and department=HR to access the HR/Payroll system, but only during active business hours within the same timezone as the company. ABAC would also define the types of actions a user can perform, such as viewing or editing files. The user’s identity and attributes are verified through authentication mechanisms before granting them access. This type of access control gives organizations a higher level of granularity when it comes to managing user permissions and defining who has access to what resources.
The Pros and Cons of Attribute-Based Access Control (ABAC)
The main advantage of Attribute-Based Access Control (ABAC) is its ability to establish access based on user attributes, rather than relying on predefined roles. This allows for more granular control over who has access to what resources, providing a higher level of security than traditional role-based access control (RBAC). Additionally, ABAC is not limited by the number of roles that can be defined and can therefore accommodate complex environments and ever-evolving needs.
However, ABAC does come with some drawbacks. The primary one is the complexity associated with implementing it in an organization. As the system is reliant on attributes and policies, there must be enough information available to allow the system to determine who should have access to what resources. Additionally, ABAC requires more management overhead as changes must be made in multiple places when policy rules or user attributes are updated. Finally, depending on the implementation, ABAC may require additional user interaction or authentication steps which could slow down performance or reduce usability.
Uses of ABAC
Attribute-based access control (ABAC) is a security model used to grant or deny access to data, network devices, and IT resources based on attributes associated with the user, the object being accessed, and the environment. ABAC uses an attribute-based policy to determine if an individual has access to a particular resource. Attributes can include the user’s role within the organization, their location, time of day, and more. With ABAC in place, organizations can create custom authorization policies tailored to their specific needs in order to ensure only authorized users are able to access sensitive resources. ABAC also provides additional benefits over traditional authorization methods such as role-based access control (RBAC), including increased scalability and flexibility when it comes to making changes or adding new policies. By creating attribute-based rules instead of relying on roles or permissions, organizations can more easily adapt to changing requirements.
The Three Primary Rules of RBAC
The three primary rules for RBAC are:
1. Separation of Duties: This rule ensures that no single user has access to all areas of the system. This helps reduce conflicts of interest and potential abuse of privileges.
2. Least Privilege: This rule states that users should only be assigned the minimum set of access rights necessary to perform their job duties. This helps protect the system from unauthorized or accidental misuse.
3. Role-Based Access Control: This rule requires each user to be assigned to a specific role that defines the access rights they can have in the system. By assigning roles, it is easier to manage who has access to what in the system, allowing for better control and security over sensitive data and resources.
What is ABAC and How Does it Relate to Cyber Security?
Attribute Based Access Control (ABAC) is a type of cyber security access control that uses attributes associated with users and resources to make decisions on granting or denying access. ABAC systems allow organizations to define specific rules that determine access rights based on set parameters, such as user attributes, role, organizational unit, geographic location, or time of day. This makes it possible to customize security policies based on the unique needs of an organization. It also allows for dynamic changes in permissions as circumstances change. Additionally, ABAC allows organizations to enforce least privilege principles by providing users with only the rights they need in order to perform their job functions.
Understanding ABAC in Cyber Security
ABAC (Attribute-Based Access Control) is an access control method that uses attributes to determine whether a user can access a system, resource, or file. The attributes can be related to the user themselves (e.g., their role in the organization), the resource they are attempting to access (e.g., its location), and environmental conditions (e.g., geographic location). ABAC uses a set of policies that define how these attributes should interact with each other, and how they should affect a user’s ability to access systems or resources. This makes it more flexible than traditional access control methods, as it allows for more granular control over who has access to what. Additionally, ABAC is often used in combination with other security measures such as authentication and authorization, making it an important part of any comprehensive cybersecurity strategy.
Conclusion
In conclusion, RBAC and ABAC are two popular access control methods used to secure data. RBAC grants access based on the user’s role within an organization, while ABAC grants access based on attributes associated with the user, resource, and environment. Both methods have their strengths and weaknesses which must be taken into consideration when deciding which one is best for a particular organization. However, when the workgroups have a simple structure with few roles, RBAC is generally preferred since it requires less time to define the attributes needed for the system to function.