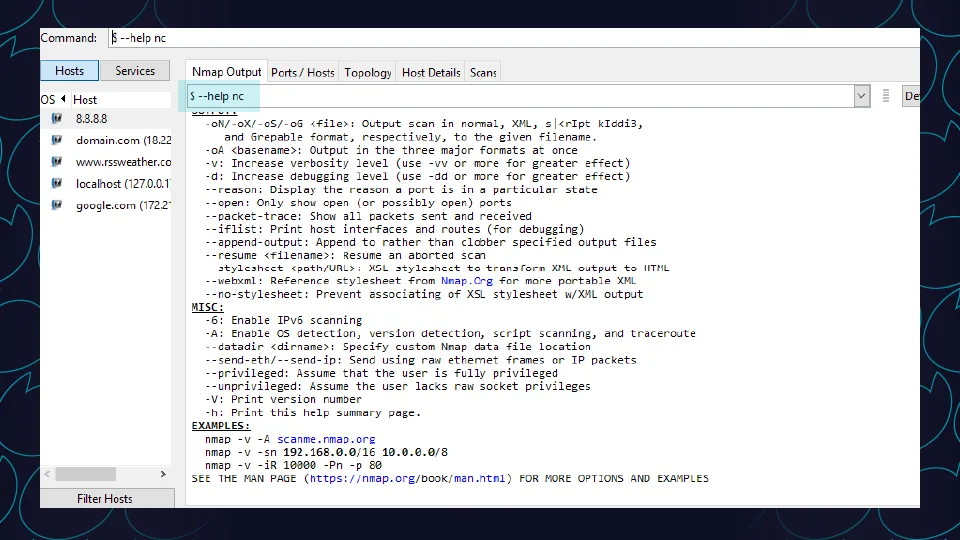
Netcat is a powerful networking tool that can be used for a variety of purposes, ranging from port scanning to file transfer. It is commonly referred to as the “Swiss army knife of networking” due to its versatility and flexibility. If you are looking to become an expert in using Netcat, you will want to familiarize yourself with all the commands and options available. To help make that process easier, we’ve compiled this comprehensive Netcat cheat sheet.
First off, it’s important to understand the basic syntax of the Netcat command. The following command will establish a connection from the local machine to a remote host on port 80:
nc -vn 80
The -v option turns on verbose output, which provides additional information about what is happening during the connection attempt. The -n option tells Netcat not to use DNS for name resolution and use IP addresses instead. The port number should be specified after the hostname or IP address.
Next up are some of the most useful options available in Netcat. Here are some of them and how they can be used:
• -z: This tells Netcat to enter zero I/O mode, which means it doesn’t send or receive any data once a connection is established. This can be used for port scanning purposes by attempting connections on each specified port until one succeeds or fails.
• -L: Specifies that once a connection is established, it should remain open until explicitly closed by sending an EOF (end-of-file) signal with Ctrl+D or Ctrl+Z. This is useful for setting up persistent tunnels between two machines without having to keep re-establishing new connections each time data needs to be sent through them.
• -e: Specifies an executable program that should be launched after a successful connection has been established with another machine. This allows you to run programs remotely over your network without having to physically access them first from their location on another machine.
• -w: Sets the time-out value in seconds before closing a connection if no response is received from either side during that period of time. By default, this value is 30 seconds but can be set lower if desired for faster response times during scans or other processes across multiple machines over your network where speed matters more than accuracy in results returned by scans or other operations taking place across multiple machines over your network where speed matters more than accuracy in results returned by scans or other operations taking place across multiple machines over your network where speed matters more than accuracy in results returned by scans or other operations taking place across multiple machines over your network..
Finally, there are two additional options worth mentioning when using Netcat: –4 and –u. The –4 option forces IPv4 version addresses instead of IPv6 while –u specifies UDP traffic as opposed to TCP (default). That covers all of the most important commands and options available when using Netcat! With these tools at your disposal, you should have everything you need for completing complex networking tasks within reach!
Uses of Netcat
Netcat is a networking utility used for reading and writing data across networks. It can be used for a variety of purposes, including port scanning, transferring files, setting up backdoors, implementing port forwarding, creating tunnels, and more.
Port scanning is one of the most common uses for Netcat. By sending specially crafted packets to a range of ports on a remote host, Netcat can detect which ports are open and accessible from the attacker’s machine. This information can then be used to exploit vulnerable services running on those ports.
Netcat can also be used to transfer files between computers. This is done by sending the file content as stdin (standard input) through a TCP/IP connection or a UDP/IP datagram connection using the -w option to specify the timeout in seconds.
Netcat has also been used to set up backdoors on compromised hosts by listening on a particular port and waiting for incoming connections from attackers. When an attacker connects to that port, they have full access to the compromised system. This allows attackers to gain remote access without authentication or authorization.
Netcat can also be used for port forwarding and tunneling through firewalls and NATs (network address translation). This allows attackers to bypass network security measures such as packet filtering rules which restrict certain types of traffic from entering or leaving networks.
In short, Netcat is an incredibly versatile tool that can be used in many different ways depending on your needs. From port scanning and backdooring systems to tunneling through firewalls and transferring files between computers, it is an essential tool for any security professional or hacker looking for an easy way to work with networks.
Using Netcat for Port Scanning
Netcat can be used to scan for open ports on a system. To use Netcat for port scanning, you need to use the ‘nc’ command with the ‘-z’ option to specify port scanning mode. You can also add other options such as ‘-v’ for verbose output, ‘-n’ to use numerical IP addresses instead of DNS names, ‘-w 1’ to set a timeout value of 1 second, and ‘-u’ to use UDP instead of TCP. If you want to force IPv4 version addresses, you can also add the ‘-4’ option. To scan a specific port or range of ports on a system, you would enter the following command: nc -zvn hostname/ip address portnumber(s). For example, if you wanted to scan ports 21 trough 25 on a system with the IP address 192.168.1.1, you would enter nc -zvn 192.168.1.1 21-25. This will give you an output telling which ports are open and which are closed on that system.
Writing a Netcat Command
To write a Netcat command, you must first start with the identifier “netcat” or “nc” as a shorter option. After this, you will need to specify the target hostname or IP address that you want to connect to. You can then decide which type of port connection you would like to use (default is TCP), and which port number you would like to use (default is port 23). Finally, once everything is set up, the command should look something like this:
nc [hostname/IP] [port number] [option parameters]
Option parameters can include adding “-u” for UDP traffic instead of TCP, “-v” for verbose output, “-p” to specify a specific port, and “-D” to turn on full debugging mode. Once all of these components are in place, your command should be ready to run.
Understanding Netcat and its Functionality
Netcat is a powerful tool that provides a connection between two computers using the TCP/IP protocol. It can be used to transfer data between machines, as well as to perform port scanning, port forwarding, and network service requests. Netcat operates in two modes – “listen” mode and “connect” mode – depending on the command line arguments given.
When Netcat is run in listen mode, it creates a listening socket on the specified port. When a connection request is made from the remote system, the local machine will respond by creating a socket and establishing a connection with the remote machine. The local machine can then send traffic to the remote computer over this connection.
When Netcat is run in connected mode, it attempts to establish a connection with the specified host and port. Once connected, Netcat can be used to send data back and forth between both computers or used as an interactive shell session.
Netcat can also be used for more advanced tasks such as setting up secure tunnels for transferring data or even performing distributed denial-of-service (DDoS) attacks on other networks. It has been described as “the Swiss Army Knife of networking tools” due to its versatility and wide range of uses.
Do Hackers Utilize Netcat?
Yes, hackers do use Netcat. It is a powerful tool used by many hackers due to its flexibility and ease of use. Netcat can be used to quickly set up remote shell access, port scanning, file transfers, and even network analysis. It also provides a number of security features such as encryption and authentication that make it attractive to hackers. Additionally, as an open-source tool, it is easily obtained and used for malicious purposes. By utilizing Netcat’s various capabilities, hackers can gain access to networks and systems or perform reconnaissance activities without being detected. Ultimately, the use of Netcat by hackers depends on their own personal objectives which may range from reconnaissance activities to more destructive attacks.
Checking If a Port is Open Using Netcat
In order to check if a port is open using netcat, you can use the command ‘nc’ followed by the domain/server IP / server hostname (temporary URL excluding the username), port number, and the parameters -z and -v. This will scan the designated port without sending data while providing verbose information. For example nc domain.com 80 -z -v. This command will attempt to connect to port 80 on domain.com, while providing verbose output and not sending any data. The output should tell you if the port is open or closed.
Is Netcat a UDP or TCP Protocol?
Netcat is a versatile networking tool that can be used for a variety of tasks, including port scanning, file transfers, and setting up network connections. By default, it uses the Transmission Control Protocol (TCP) for communication, but it can also use User Datagram Protocol (UDP) with the -u option. With UDP, Netcat can be used to set up both client-server and peer-to-peer connections.
Number of Modes in Netcat
Netcat has two modes: client mode and listen mode. In client mode, Netcat can be used to initiate a connection to any TCP or UDP port on another system. In listen mode, Netcat opens any TCP or UDP port on the local system and waits for data to come in through that port.
Connecting to a Port with NCAT
To connect to a port with Ncat, you will first need to open the command line and run the command ‘ncat [destination IP] [port]’. This will establish a connection between your machine and the specified destination at the given port number. You can also use the ‘-l’ flag to set up a listening port on your machine and have Ncat wait for a connection from another machine. Once this is done, you can then connect from the other machine using ‘ncat [source IP] [port]’, and any data sent over this connection will be handled by Ncat.
Does Netcat Open Ports?
Yes, netcat can open a port. Netcat is an incredibly versatile utility that can be used to establish connections on any TCP or UDP port. It can also be used to create and listen on arbitrary ports, send UDP packets, and perform port scanning under both IPv4 and IPv6. To open a port with netcat, you would use the command ‘nc -l ’ which is the number of the port you wish to open. Once the port is opened, it will wait for inbound connections from remote systems until you terminate it with Ctrl + C. Additionally, netcat can also be used to connect to already opened ports on remote systems by specifying the hostname and port number as arguments to the ‘nc’ command (e.g., ‘nc ’).
Conclusion
In conclusion, Netcat is a powerful and versatile networking tool that can be used to read and write data across both TCP and UDP connections. It features several useful options, such as “-u” for UDP traffic instead of TCP, “-v” for verbose output, “-p” to specify a specific port, and “-D” to turn on full debugging mode. With these options and its secure back-end capabilities, Netcat is an invaluable tool for any network administrator or security professional.