Are you looking for a way to install Nmap on your Mac computer? Nmap is a powerful network security scanner that can be used to detect and identify open ports, running services, and system vulnerabilities. It is an open-source tool and is available for free to all users. In this blog post, we will discuss how to install Nmap on your Mac computer.
First off, it’s important to note that there are two main versions of Nmap: the command line version (Nmap) and the graphical user interface version (Zenmap). For most users, the graphical version is recommended as it makes the scanning process easier and more user-friendly.
The easiest way to install Nmap and Zenmap on Mac OS X is to use our installer. The Mac OS X section of the Nmap download page provides a file named nmap-. The contents of the disk image will be displayed when you open it. Follow the instructions in the installer in order to complete the installation process.
Once you have installed Nmap, there are several commands that you can use in order to start scanning your network for potential security vulnerabilities. For example, you can use “nmap linuxhint.com” in order to scan Linuxhint’s website for any potential threats or vulnerabilities. You can also use “sudo nmap 192.168.18.68” in order to scan an IP address or range of IP addresses for any potential vulnerabilities as well as “sudo nmap -O linuxhint.com” which will scan Linuxhint’s website for operating systems that may be running on it and their versions.
Finally, it’s important to note that while Nmap is generally a safe tool, there may be some restricted environments where installing it is against policy or law due to its ability to find potential security flaws in systems connected with a given network or server address range (e.g., government networks). If you plan on using Nmap in such an environment, make sure you first consult with your organization’s IT department before proceeding with its installation and usage so as not to violate any rules or regulations within that environment.
We hope this blog post helped answer any questions you may have had about installing NMap on your Mac device!
Installing Nmap on a Mac
Installing Nmap and Zenmap on Mac OS X is easy and straightforward. First, go to the Nmap download page and locate the file named nmap- in the Mac OS X section. Download this file, then open it to mount the disk image. The contents of the disk image will be displayed. Follow the instructions in the installer to complete your installation. After it is finished, you can use Nmap to scan your network for security vulnerabilities.
Installing Nmap in Terminal
Installing Nmap in the terminal is a relatively simple process. To begin, open up your terminal and enter the command “sudo apt install nmap”. This command will start the installation process for Nmap, which will include downloading and installing the necessary files. Depending on your internet connection speed, it may take a few minutes to complete the installation. Once it has finished, you can then use Nmap in your terminal by entering commands such as “nmap linuxhint.com” or “sudo nmap 192.168.18.68”. With Nmap installed, you can now use it to perform network scans and security tests on your local network or any other connected devices.
The Benefits of Installing Nmap
The answer to whether or not you should install Nmap depends on your needs and the environment in which you are working. Nmap is a powerful tool that can be used by cybersecurity professionals to identify vulnerabilities in networks and systems. It is a great way to assess the security of your own environment, as well as to scan for potential threats from outside sources. However, it is important to note that Nmap may not be appropriate for all situations.
If you are using Nmap in an enterprise setting, it is important to ensure that it does not violate any policies or regulations within your organization. Additionally, if you are scanning a public network or system, it is important to ensure that you have permission from the owner of that system before running any scans.
Finally, even if Nmap is perfectly safe and compliant with your organization’s policies and regulations, there may still be other risks associated with running scans on other networks. For example, if your scan generates too much traffic or triggers any alarm systems, it could result in unwanted attention from potential attackers or security personnel.
Overall, if used properly and within the guidelines of your organization’s policies and the laws of the country where you are running scans, then Nmap can be a very useful tool for assessing the security of networks and systems. However, it is important to consider all possible risks before deciding whether or not to install this powerful tool.
Does Nmap Provide MAC Addresses?
Yes, Nmap can give you the MAC address of hosts on a local Ethernet LAN. It does so by reading the headers of the network traffic that is sent to and from the host. This is a useful tool for network administrators who need to identify which devices are connected to their network, as each MAC address is unique and can be used to track down a particular device. Nmap also provides other information such as open ports and services running on hosts, which can be used to further investigate a device or network.
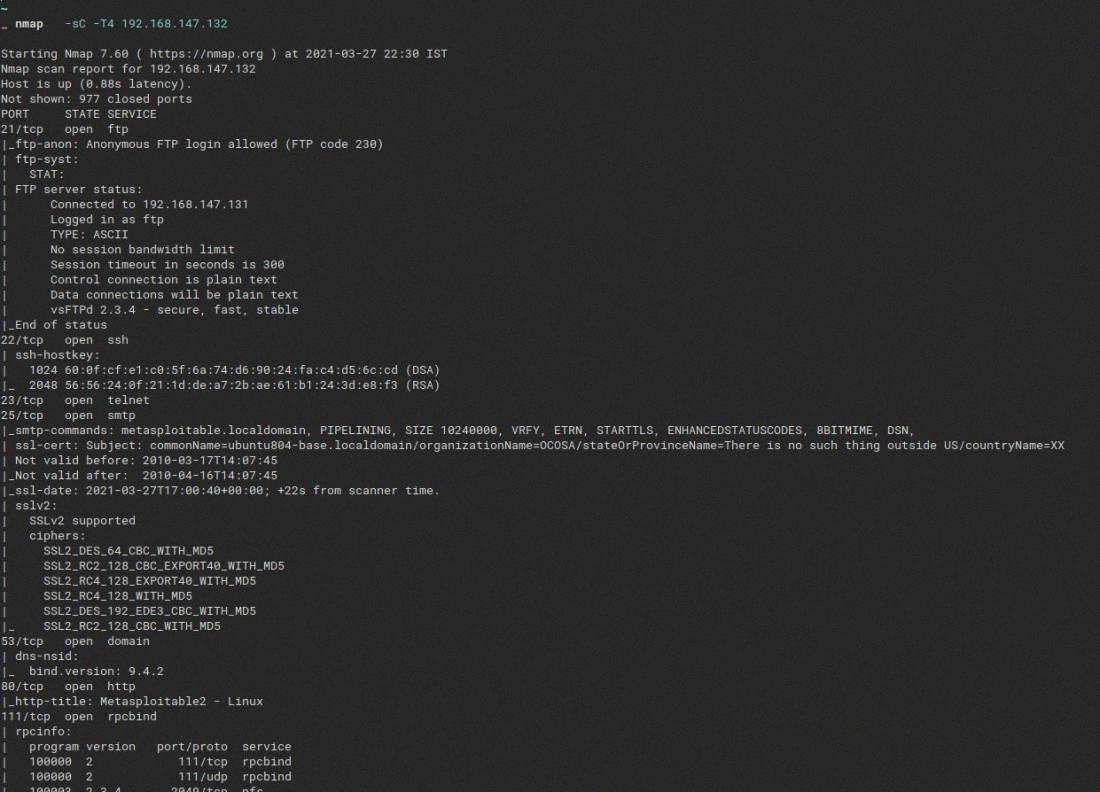
Source: geeksforgeeks.org
Is Nmap a Free Software?
Yes, Nmap is completely free to use. It is open-source software released under the GNU General Public License (GPL), meaning it is free for anyone to download, use, modify, and redistribute. The source code is available on GitHub and can be used for both commercial and non-commercial purposes. Additionally, Nmap has been around since 1997, making it one of the oldest and most trusted network security tools in the industry.
Conclusion
In conclusion, Nmap and Zenmap are essential tools for any cybersecurity professional on Mac OS X. With the Nmap installer, users can easily download and install the software on their system with a few simple steps. Users should take care to read the instructions in the installer carefully before proceeding, in order to ensure that they have the most up-to-date version of the software installed. Although it is generally safe to use, there may be some restricted environments where it is against the rules to install it.