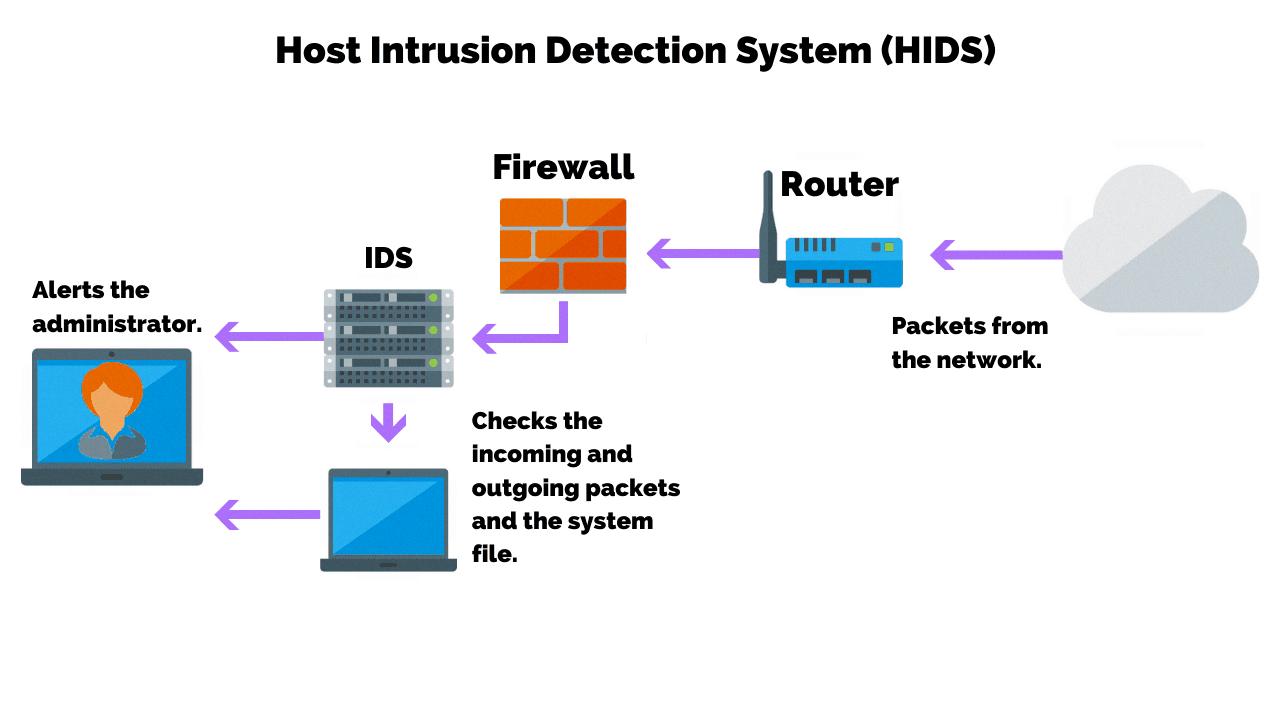
Host-based Intrusion Detection Systems (HIDS) are designed to detect and prevent malicious activity on a specific system or network. They are typically deployed as part of a larger security solution, such as an Application Security Platform, to provide additional layers of protection from malicious actors. HIDS monitors systems for suspicious behavior and can be used to detect attempts at unauthorized access, malicious code, and other forms of attack.
HIDS solutions can be divided into two main types: active HIDS and passive HIDS. Active HIDS solutions actively monitor systems for suspicious activity, whereas passive HIDS solutions passively monitor systems for changes in their configuration or activity. Active HIDS solutions are typically more effective at detecting attacks in real-time, while passive HIDS solutions are better suited to detecting intrusions after they have occurred.
Active HIDS solutions use a variety of techniques to detect suspicious activity on the system being monitored. These include signature-based detection, which looks for known patterns of malicious activity; anomaly-based detection, which looks for deviations from normal behavior; and heuristic-based detection, which looks for activities that do not match any known patterns but may still indicate an attack.
In addition to these active techniques, passive HIDS solutions also look for changes in a system configuration that might indicate an attack has taken place. For example, some passive solutions might look for changes in the registry or file permissions that could indicate malicious access or modification of files. Additionally, some passive solutions might scan log files looking for unusual access attempts or other signs of attack.
Finally, it is important to note that no single security solution can provide total protection from all threats – but when combined with other security measures such as firewalls and antivirus software – a well-designed HIDS solution can provide a significant layer of defense against malicious actors seeking to gain unauthorized access to your networked systems or data.
Differences Between NIDS and HIDS
Network Intrusion Detection Systems (NIDS) and Host Intrusion Detection Systems (HIDS) are both security solutions that detect malicious activity on a network. However, the two systems differ in how they operate and what they are used for.
NIDS is designed to monitor an entire network for suspicious activity. It works by continually scanning traffic for malicious or anomalous patterns and alerting administrators when something suspicious is detected. NIDS works in real-time, meaning it tracks live data and flags potential issues as they happen.
HIDS, on the other hand, is designed to monitor individual computers or servers for suspicious activity. It does this by examining logs of past activities to detect any unusual or malicious behavior that might have occurred after the initial scan of the system by NIDS. HIDS can also be used to detect sophisticated hackers who use non-conventional methods that may be difficult to catch in real time with NIDS.
Source: liquidweb.com
Examples of Host Intrusion Detection Systems (HIDS)
Host-based Intrusion Detection Systems (HIDS) are specialized security solutions that monitor, detect, and respond to malicious activity and system misconfigurations on a single computer or server. HIDS are typically used to protect an organization’s most critical and valuable assets, such as servers and databases. Examples of popular HIDS solutions include OSSEC, Quadrant, Splunk, Snort, and Tripwire.
OSSEC is one of the most popular open-source HIDS solutions available. It provides file integrity monitoring, log analysis, rootkit detection, and active response capabilities. It can be deployed in both Windows and Linux environments.
Quadrant is another popular HIDS solution focused on detecting anomalous activities in both cloud and on-premise environments. It uses machine learning algorithms to identify suspicious behavior patterns in user access logs. Quadrant also offers automated incident response capabilities for responding quickly when threats are detected.
Splunk is a powerful HIDS solution that enables organizations to manage data from multiple sources including network devices, application logs, cloud infrastructure assets, web transactions, and more. It provides real-time visibility into suspicious activity so users can take action quickly when threats are detected.
Snort is an open-source intrusion detection system (IDS) designed specifically to detect malicious activities at the network level. It monitors incoming traffic for suspicious patterns that may indicate malicious intent or compromise attempts against network assets. Snort also has the ability to block malicious traffic before it can do any damage.
Tripwire is another popular HIDS solution that focuses on detecting unauthorized changes to systems files or configurations by comparing a known baseline with the state of the system at regular intervals. If any discrepancies are found between the two states then it triggers an alert allowing admins to take action quickly before any damage is done.
Types of Host-Based Intrusion Detection Systems
The three main types of HIDs (High-Intensity Discharge) lamps are Mercury, Sodium, and Metal Halide. Mercury HIDs produce bright white light with excellent color rendering, making them ideal for general light or task lighting applications. Sodium HIDs are most commonly used in outdoor lighting applications due to their yellow-orange light output and high efficiency. Finally, Metal Halide lamps are often used in commercial and industrial lighting applications because they offer the highest efficiency of all HID lamp types, and they can be used to produce a range of color temperatures.
Advantages of Using HIDS Over NIDS
The primary advantage of using a Host-Based Intrusion Detection System (HIDS) over a Network-Based Intrusion Detection System (NIDS) is that HIDS provides greater granularity and flexibility when it comes to monitoring system activities. Specifically, HIDS can be tailored to the specific needs of each host or system it is installed on, allowing it to better detect malicious activity that is unique to that particular environment. Additionally, HIDS can monitor system logs, application logs, and other sources of data in order to detect threats and malicious activities.
In comparison, NIDS is more limited in what it can monitor since they are designed to only monitor network traffic. While NIDS can detect some malicious activities at a network level, they cannot provide the same level of detailed analysis as HIDS. Furthermore, since NIDS must analyze all network traffic on a segment, they can require more resources than HIDS and be more prone to false positives.
The Advantages of a Host-Based Intrusion Detection System (HIDS)
A Host-based Intrusion Detection System (HIDS) offers a number of advantages over Network-Based Intrusion Detection Systems (NIDS). One of the most significant benefits of HIDS is that it can detect attacks that cannot be seen by NIDS since it monitors events local to a host. Additionally, HIDS can often operate in an environment where network traffic is encrypted and unaffected by switched networks. This makes them ideal for use in environments where sensitive data needs to be kept secure.
Comparing HIDS and IPS
HIDS (Host-based Intrusion Detection System) is a type of Intrusion Detection System (IDS) that is installed on a single host or virtual machine and is designed to detect malicious activity on that particular system. HIDS works by analyzing events such as logins, file access, resource usage, and other activities to identify patterns or changes in behavior that may indicate the presence of a malicious actor. It does not actively prevent any malicious activity from occurring, but it can be used to alert administrators so they can take steps to protect their systems.
HIPS (Host-based Intrusion Prevention System) is an IPS that runs on a single host or virtual machine and is designed to detect and block malicious activity before it has the opportunity to cause harm. HIPS works by actively monitoring for suspicious activities, such as attempts to access restricted files or resources, and then blocking them before any damage can occur. It also makes use of signatures and rules in order to quickly detect known threats and take appropriate action. Whereas HIDS can only alert administrators after the fact, HIPS is able to take proactive steps in preventing malicious actors from doing any harm.
Difference Between HIDS and Firewall
A HIDS (Host Intrusion Detection System) is a security system that monitors and detects changes or suspicious activity on a computer or network. It works by analyzing system events such as file access, user logins, and application usage and can detect malicious activity such as unauthorized logins, data theft, malicious code execution, etc. A HIDS is typically used to supplement existing security measures such as firewalls or antivirus software.
A firewall is a network security system that allows or denies traffic between the computer and other systems. It can be either hardware- or software-based and is designed to protect the network from unauthorized access. Firewalls are typically used to block malicious traffic from entering the network, but can also be configured to allow certain types of traffic through. Firewalls can also monitor incoming and outgoing traffic for malicious activities such as port scans or suspicious packets.
Is Splunk a Host-Based Intrusion Detection System?
Yes, Splunk is a Host-based Intrusion Detection System (HIDS). It can be used to detect malicious activity on a single host or computer system, such as unauthorized access, tampering with files, suspicious changes in data and system logs, and other malicious behaviors. Splunk provides two main features for HIDS: log monitoring and alerting. Log monitoring allows you to view all the system events in real time and identify any suspicious activities. Alerting allows you to set rules that trigger notifications when certain conditions are met. The base package of this tool is free to use and it doesn’t include any network-based data alerts, so it is a pure HIDS. If you are looking for an anomaly-based HIDS, this is a very good option.
Differences Between HIDS and Antivirus
The primary difference between a Host Intrusion Detection System (HIDS) and an anti-virus solution is the scope of protection they provide. An anti-virus solution typically focuses on detecting, blocking, and removing malicious files from the system. A HIDS, however, provides a broader level of protection by tracking changes to the file system, analyzing log files for suspicious activity, and monitoring user access privileges. Additionally, HIDS solutions can often detect malicious activity even if the malicious code has not yet been identified by anti-virus vendors. In summary, HIDS provides a more comprehensive approach to system security by combining multiple layers of protection in order to better detect and prevent suspicious activity.
Conclusion
In conclusion, HIDS is an effective security solution for organizations of any size that need to ensure their data is protected. This type of system is efficient and cost-effective, as it can detect malicious activity in real-time and prevent it from causing major damage. Additionally, the different types of lamps used in HIDS allow for a tailored approach when it comes to choosing the right security solution. Finally, antivirus protection can provide additional levels of protection against malicious threats, making HIDS an even more reliable form of security.