Have you ever connected to a public Wi-Fi network and wondered if someone might be trying to steal your data? If so, you are not alone. An evil twin Wi-Fi attack is a type of spoofing attack that can potentially expose users to malicious hackers. In this blog post, we will discuss what an evil twin attack is, how it works, and how you can protect yourself from these types of attacks.
An evil twin attack is a type of man-in-the-middle (MITM) attack where a malicious actor creates a rogue access point with the same name as the legitimate public Wi-Fi network. The attacker then lures unsuspecting users into connecting to this fake network in order to steal their data.
The attacker typically sets up the rogue access point somewhere close enough for it to appear on the list of available networks when users attempt to connect. Once they connect, they unwittingly give away their login credentials and other sensitive information that may be transmitted over the network.
Another way an attacker can execute an evil twin attack is by deauthenticating users from the legitimate access point and forcing them onto the rogue access point. This technique can be used to trick even savvy users into connecting because they don’t know any better — after all, why wouldn’t they trust a known Wi-Fi network with an identical name?
Thankfully, there are some ways you can protect yourself from falling prey to an evil twin attack. First, always double-check that you are connected to the correct Wi-Fi network before entering any sensitive information or credentials. Second, if you see a lock icon next to your connection in your device’s settings menu, it means that your connection is secure — meaning that no one else can use it without permission from you or another authorized user. Third, use comprehensive security software like Avast One which offers protection against multiple types of online threats including man-in-the-middle attacks like evil twin Wi-fi networks.
In conclusion, an evil twin Wi-Fi attack is a type of man-in-the-middle (MITM) attack where hackers create fake access points in order to steal user data such as login credentials and credit card information. Thankfully there are measures you can take in order to protect yourself from falling victim such as double-checking your connection before entering any sensitive information and using comprehensive security software like Avast One which offers protection against these types of attacks.

Does the Evil Twin Attack Utilize Wi-Fi?
Yes, an evil twin attack uses Wi-Fi. It is a type of spoofing attack that targets unsuspecting users by creating a fake Wi-Fi access point (AP) using the same name as a legitimate one in order to deceive victims into connecting to it. The attacker then captures their data and can use it for malicious purposes. To protect against this type of attack, users should check to make sure the network they are connecting to is secure before entering any sensitive information. Additionally, comprehensive security solutions like Avast One can provide additional protection from online threats.
Example of an Evil Twin Attack
An evil twin attack is a type of cyberattack where a malicious actor sets up a fake Wi-Fi access point with the same SSID (name) as a legitimate public network. The hacker then entices unsuspecting victims to connect to their malicious copy of the network. In our example, when the victim attempts to connect to their trusted Wi-Fi network, they are actually connecting to the hacker’s evil twin. As soon as they are connected, the hacker can intercept and view all of the data that is being transmitted between the victim’s device and the hacker’s malicious access point. This allows them to gain access to sensitive information such as usernames, passwords, financial records, and more.
The Use of Evil Twin by Hackers
Yes, hackers can use an evil twin attack to gain access to personal user data. An evil twin attack is a type of cyberattack in which a hacker creates a fake Wi-Fi network with the same name as another legitimate network. When unsuspecting users connect to the fake network, the hacker can steal their data, including login credentials, bank transactions, and credit card information. The hacker may also use this data to launch additional attacks on other accounts or networks. In some cases, they may even be able to take control of devices connected to the malicious network. Because many users do not take the time to check if they are connecting to a legitimate Wi-Fi network, evil twin attacks can be very effective for hackers looking to access sensitive information.
The Definition of Wi-Fi Sniffing
Wi-Fi sniffing is a process by which a wireless network is scanned and monitored to intercept data packets and capture information. This information can then be analyzed to gain insights into what is happening in the network. Wi-Fi sniffers are used to identifying security risks, monitor user activity, troubleshoot network issues, and much more. By understanding how data is transmitted over a Wi-Fi network, it becomes easier to protect systems from malicious attacks.
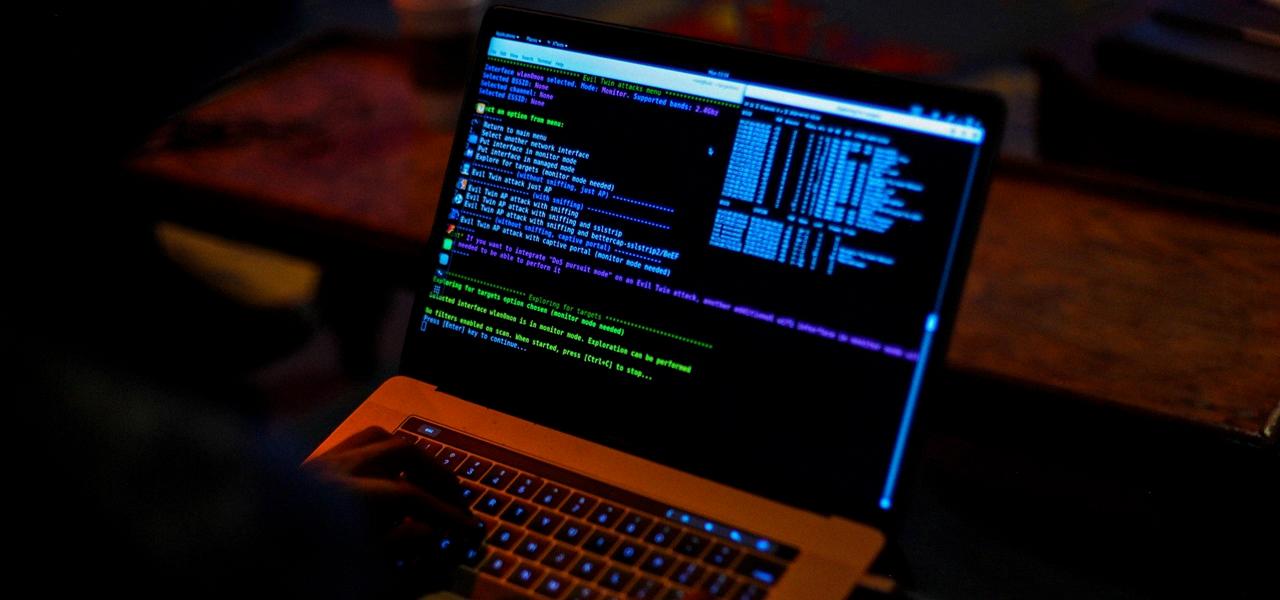
Source: null-byte.wonderhowto.com
Types of Attacks Used by Hackers on Free Wi-Fi
Hackers can use a variety of attacks on free Wi-Fi networks, the most common being man-in-the-middle attacks. In a man-in-the-middle attack, the hacker intercepts data traveling between your device and the Wi-Fi router, which is often unencrypted on public networks. The hacker can then access or modify that data as it passes through. Other attacks used by hackers on free Wi-Fi include packet sniffing, which involves eavesdropping to capture sensitive data transmitted over the network; rogue access points, which trick users into connecting to malicious networks; and session hijacking, where the hacker takes over an existing connection between two devices.
Defending Against an Evil Twin
To defend against an evil twin, you should take the following precautions:
1. Avoid connecting to public Wi-Fi networks unless absolutely necessary, as these are more vulnerable to attack.
2. Turn off your device’s Wi-Fi when it’s not in use.
3. Use a virtual private network (VPN) to encrypt all of your data when connected to a public network.
4. Be careful when connecting to a public Wi-Fi network, as some malicious actors may set up their own fake networks with similar names. Always check the name of the network and confirm that it is legitimate before connecting to it.
5. When connecting to a public Wi-Fi network, make sure that the website you’re accessing is secure by looking for “https” at the beginning of its URL address instead of just “HTTP” which indicates an unsecured connection.
6. Consider using two-factor authentication for your accounts, which requires you to provide an additional code after entering your username and password in order to access them. This will help protect your accounts from hackers even if they have access to your credentials through an evil twin attack.
Conclusion
In conclusion, an evil twin Wi-Fi attack is a type of spoofing attack that attempts to trick victims into connecting to a malicious access point. The hacker sets up a fake access point, often with the same SSID name as the legitimate network, in order to steal personal data like login credentials, bank transactions, and credit card information. By de-authenticating users from the real access point, the hacker can force them to enter their password into the fake access point. To protect against such attacks, users should be aware of potential security threats and take measures such as using comprehensive security software like Avast One.