An event log analyzer is a powerful tool for proactively managing your IT infrastructure. With EventLog Analyzer, you can easily review and analyze computer-generated event logs to identify potential bugs, security threats, or other risks. This cost-effective SIEM solution provides comprehensive log management, compliance reporting, user activity monitoring, file integrity monitoring (FIEM), log aggregation, log forensics, and log retention capabilities.
Using EventLog Analyzer is simple and straightforward. To get started, open the Event Viewer and expand the Windows Logs section. From there, click on Security to populate the security events list. In the Actions area of the window, select Filter Current Log and enter an Event ID in the All Event IDs field; for example 4624. Finally, click OK and save the filtered log file to your preferred location.
EventLog Analyzer offers convenient features such as automatic alerting when suspicious events are detected and customized reports with real-time insights into user activity trends. It can also be used to ensure compliance with regulations and audit user behavior in order to protect your network from potential threats or malicious activity.
The best part about EventLog Analyzer is that it’s free for 30 days; after this period it will automatically convert to a free edition unless you purchase a license for the premium version. So why not give EventLog Analyzer a try today? With this powerful tool in your arsenal, you’ll be able to stay ahead of any potential security issues or risks that could jeopardize your business or personal data!
The Benefits of Event Log Analysis
Event log analysis is a process used to identify and analyze computer-generated events such as errors, warnings, or security threats. Log analysis involves collecting and reviewing event logs from various sources such as system logs, application logs, and security logs. The goal of log analysis is to proactively identify potential issues in order to prevent costly outages or security breaches. It can also be used to review user behavior or ensure compliance with regulations. Event log analysis typically employs automated tools to help identify patterns in the data that may indicate a problem or potential risk. Once identified, these patterns can be further investigated by a team of experts who can take appropriate corrective action.
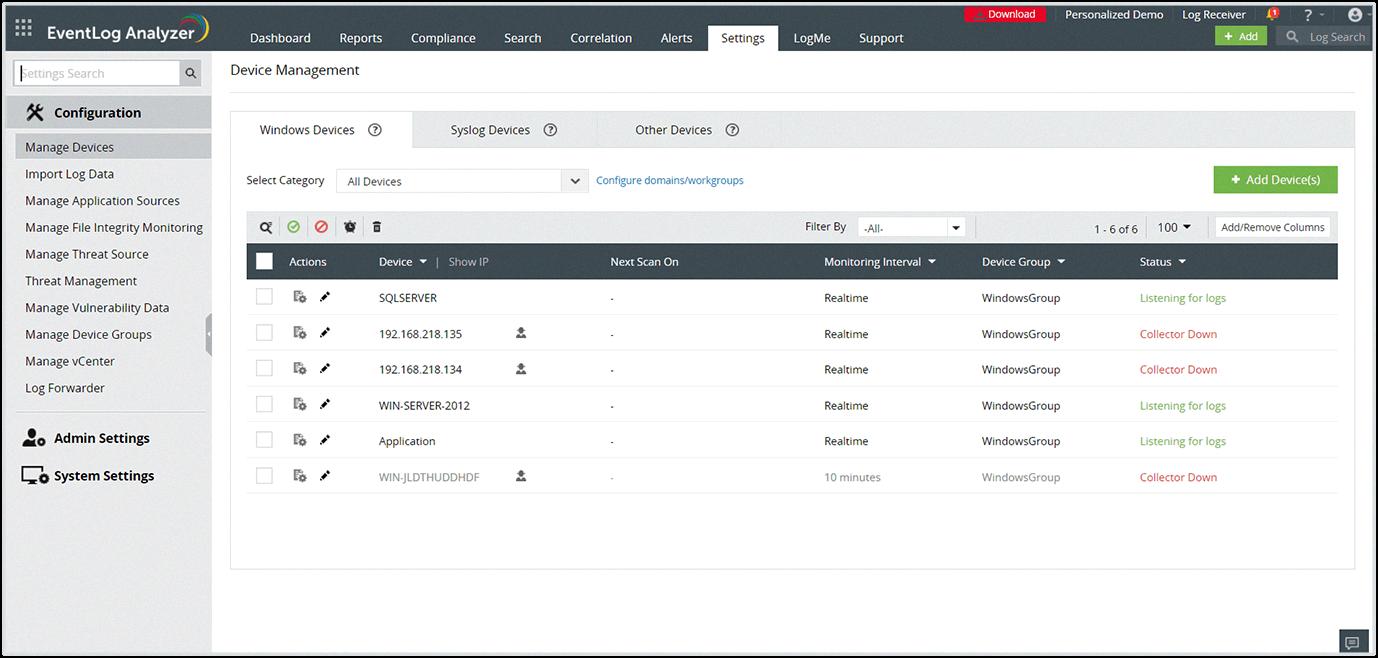
Source: manageengine.com
Is EventLog Analyzer a Security Information and Event Management (SIEM) Solution?
Yes, EventLog Analyzer is a Security Information and Event Management (SIEM) solution that provides powerful log aggregation and correlation capabilities to help protect IT infrastructures. It includes features such as compliance reporting, file integrity monitoring, user activity monitoring, log forensics, and log retention. EventLog Analyzer also offers an affordable alternative to other SIEM solutions on the market. Its easy-to-use interface and wide range of features make it the perfect fit for businesses of all sizes.
Analyzing Windows Event Logs
Analyzing Windows event logs is an important part of understanding the state of your system and detecting any potential problems. To analyze event logs, first, open the Event Viewer in the Control Panel. Expand Windows Logs and click on Security to view the security events. In the Actions area, select Filter Current Log. This will allow you to filter events by specific criteria such as Event ID or date range. Once you have set up your desired filters, click OK and then Save Filtered Log File As to save the filtered results for further analysis. You can then use third-party software such as Splunk or ELK stack to analyze and visualize the log files. Additionally, you can use Windows PowerShell scripts to parse event log data and extract meaningful insights from it.
Is ManageEngine EventLog Analyzer Offered for Free?
ManageEngine EventLog Analyzer is free for a trial period of 30 days. After this period, it will automatically convert to the Free Edition unless you purchase a license for the Premium Edition. The Free Edition offers users the ability to access log data from up to five sources, monitor real-time logs, and create reports and alerts for proactive security. The Premium Edition offers additional features such as log archival, advanced analytics, PCI Compliance Reports, and more.
Understanding How an Event Log Works
Event logs are an important tool for understanding the performance and operations of computer systems and applications. Event logs record information about system activity, including system start-up, application errors, and security issues, such as failed login attempts. Event logs can be used to troubleshoot problems, identify trends in system performance, or analyze security events.
When an event occurs on a system or application, the log records the time of the event and the user or process that triggered it. This data is stored in a formatted text file which can be accessed by security professionals or automated security systems like SIEMs. By analyzing these log files, IT administrators can identify potential security threats, investigate performance issues and generate reports to track changes over time.
Event logs can also be used to monitor user activity on a system. Logs will record what actions users are taking on a system or application and who is accessing certain resources. This information can then be used to create detailed user activity reports for auditing purposes.
Overall, event logs provide valuable insight into how systems and applications are being used, helping organizations make informed decisions about their IT infrastructure and ensure secure operations.
Is the Security Information and Event Management (SIEM) System Still Relevant?
SIEM is not outdated technology; rather, it has adapted to the changing needs of organizations in the face of increasingly dynamic threats. SIEM systems have been enhanced over time to provide better visibility into networks and applications, as well as greater detection and response capabilities. They are now capable of collecting and analyzing data from a wide range of sources, including cloud-based services, mobile devices, and even Internet of Things (IoT) devices. This data can then be used to identify patterns that may indicate malicious activity or other security threats. Additionally, modern SIEMs offer automated responses that can help contain risk quickly and efficiently when potential threats are identified. In short, SIEM systems remain a valuable tool for organizations looking to protect themselves from cyber threats.
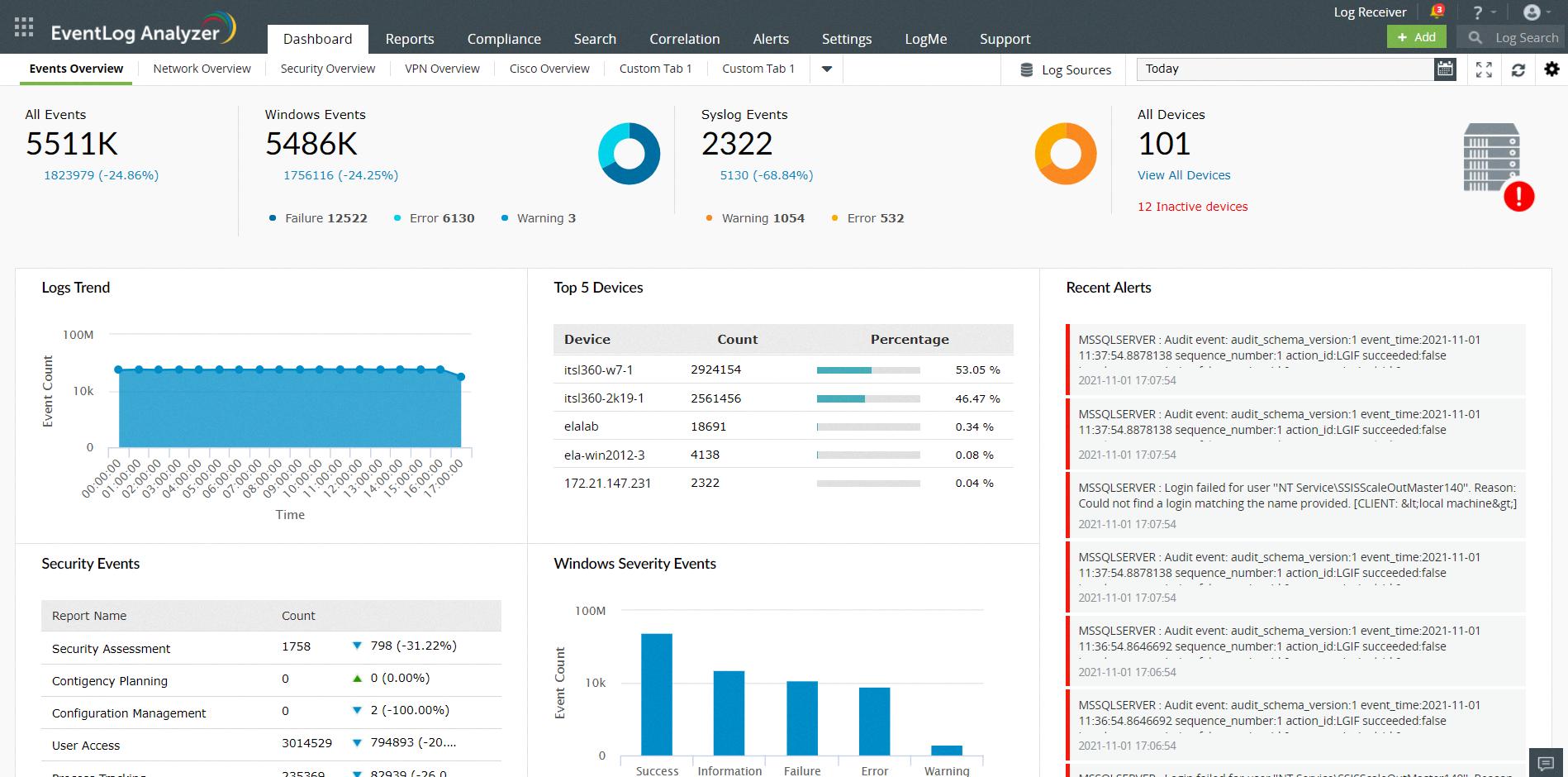
Source: softwareadvice.com
Is ManageEngine a Security Information and Event Management (SIEM) Solution?
Yes, ManageEngine is a Security Information and Event Management (SIEM) solution. It combines log management, real-time event correlation, network behavior analysis, and security incident response capabilities into one unified platform. The SIEM solution can detect malicious behavior, prioritize threats based on risk levels, investigate suspicious activities with intelligent analytics, and respond to security incidents quickly and efficiently. It also features integrated Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) capabilities to ensure comprehensive security for your organization.
Conclusion
In conclusion, EventLog Analyzer is a powerful SIEM solution that can be used to proactively identify and mitigate security threats, ensure compliance with regulations, and review user behavior. It includes features such as Compliance Reporting, File Integrity Monitoring (FIEM), User Activity Monitoring, Log Aggregation, Log Forensics, and Log Retention. EventLog Analyzer can be downloaded for free for a 30-day trial and can be upgraded to the Premium Edition if desired.