Data is the lifeblood of any organization. It is used to make decisions, drive sales, and even keep track of daily operations. But with so much data being generated and stored, it’s important to know the difference between data at rest and data in motion. To help you understand what each means and how they are related, let’s explore the differences between them.
Data at rest is any data that is stored, saved, or archived on a device or in a database. This includes files on your computer, emails in your inbox, documents stored on a server, images in an online photo album, and more. Data at rest is static and does not change unless it is manually updated or deleted by an administrator or user.
Data in motion refers to data that is actively being accessed and processed by users. This includes webpages that are loading on your computer as you browse the internet, emails as they are sent between two users, messages sent through an instant messaging platform, audio, and video streams as they are streamed across the internet, etc. Data in motion can change quickly depending on user activity and can be vulnerable to security threats if not properly protected.
Both data at rest and data in motion have their own unique set of risks associated with them. Data at rest can be vulnerable to hacks if not properly encrypted or secured; for example, a hacker could gain access to sensitive information stored on a server if it has weak security measures in place. On the other hand, data in motion can also be vulnerable to hacking if it is not properly encrypted while being sent over a network; for example, if someone were able to intercept an email message before it reached its intended recipient they could potentially gain access to confidential information contained within the message itself.
For organizations looking to protect their data from potential threats, it’s important to understand both types of data and how they work together. Organizations should ensure that all of their data – both at rest and in motion – is properly secured using encryption software or other security measures such as firewalls or antivirus programs. Additionally, organizations should regularly monitor their networks for any suspicious activity that could indicate that someone has gained unauthorized access to their systems or networks.
By understanding the differences between data at rest and data in motion you can better protect your organization from potential threats while ensuring that your users have access to the information they need when they need it most.
Data At Rest, Data In Motion, and Data In Use
Data at rest is data that is stored and not actively being used. It can reside on a hard drive, computer, database, or another storage device. This data is usually encrypted to protect it from unauthorized access. Data in motion refers to information that is actively being transferred between two or more locations; for example, data sent over the internet or via an email attachment. Data in use is data that is currently being accessed and processed by users; this could include data being read, processed, modified, or updated. Data in use typically requires stronger security measures to protect it from malicious attacks and unauthorized access.
States of Data
Data can be in one of three states: data at rest, data in motion, or data in use.
Data at rest is information that is stored and not actively being used or transmitted. Data at rest can include emails, documents, files, and databases that are stored on a computer’s hard drive or cloud storage. This type of data is usually encrypted to protect sensitive information from unauthorized access.
Data in motion refers to data that is being transmitted over a network such as the Internet. This could include emails being sent, video streams, audio streams, or any other type of data transfer from one computer to another. Data in motion is usually encrypted for security reasons as well.
Lastly, data in use refers to information that is actively being processed by a computer or application. This could include user input into an application, and calculations made by the computer using stored information such as when playing a game or running a program on the computer. Data in use may also include temporary files created during the course of processing information.
Difference Between Data In Motion and Data In Use
Data in motion refers to data that is moving across a network, while data in use is data that is actively being accessed or manipulated on a device. Data in motion typically involves transferring files from one device to another, sending emails and messages, streaming videos, and more. Data in use can involve anything from running applications to performing calculations to editing documents. In both cases, the data is not at rest and must be protected with appropriate security measures.
Difference Between Data In Flight and Data In Rest
Data in flight refers to data that is moving from one point to another and is actively being transmitted over a communications medium such as a network or the Internet. This data can be in the form of emails, images, text, video, or any other type of digital information. Data in flight is vulnerable to interception and manipulation by malicious actors so it needs to be encrypted for security purposes.
Data in rest on the other hand refers to any data that is stored or written to some type of media storage such as a disk, tape, or even cloud storage. This data can include databases, documents, spreadsheets, and other forms of digital information. Data in rest needs to be protected against unauthorized access and modification with robust security measures such as encryption and authentication mechanisms.
Examples of Data in Motion
Data in motion is any data that is actively being created, updated, or processed in a digital environment. An example of data in motion could be an email being sent from one user to another, a photo is uploaded to a cloud storage system or real-time updates on stock prices based on sensors collecting market information. Data in motion can also refer more generally to the transfer of data between different systems and networks.
Source: trailhead.salesforce.com
Examples of Data at Rest
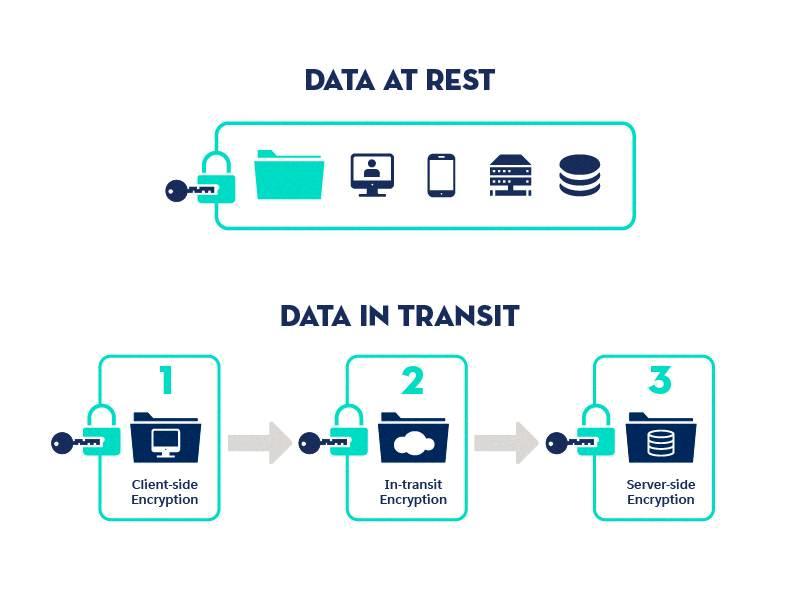
Data at rest are data stored in a non-transitory form, typically on a database server, an external backup medium such as a USB flash drive, an external hard drive or a backup storage array, a storage area network array, or a network-attached storage system and the servers of an offsite cloud backup service provider.
When data is stored on any of these devices or systems, it is said to be at rest. This means that the data is not actively being used and does not need to be accessed immediately; rather, it can be accessed when necessary.
For example, if you have created a database for your business, this information will likely be stored on a database server. The data will remain in storage until you choose to access it and use it for something. Similarly, if you have backed up your computer’s data onto an external hard drive or USB flash drive, the data will remain there until you need to use it again. Finally, if you have chosen to use an offsite cloud backup service provider to store your sensitive information, all of this data will remain securely stored in their servers until you call upon them for assistance.
Risks to Data at Rest
The main risks to data at rest are loss, leakage, or theft. Loss can occur due to hardware failure, accidental deletion, or system crashes. Leakage can occur if an unauthorized user gains access to the device or backup medium where the data is stored. Theft can occur when a malicious actor steals the device or backup medium that contains the sensitive data. In addition, data at rest is vulnerable to attack by hackers who use malware and other methods to gain access to confidential information stored on computers and other devices. Furthermore, if the data is encrypted it may still be vulnerable if encryption keys are not properly managed. To minimize these risks it is important to ensure the physical security of the device or backup medium storing the data, as well as use strong encryption techniques and secure password practices when storing sensitive information.
Understanding Data in Motion
Another term for data in motion is data in transit. Data in transit is the process of transferring digital information from one location to another, such as between two computer systems or over a network. This transfer can be done either as a physical transmission of the data or via an electronic connection, such as streaming data over the internet. Data in transit is also sometimes referred to as data in flight.
Conclusion
In conclusion, data is an important part of our lives and is constantly changing states. Data at rest is information stored in a database or on a hard drive, computer, or portable device. Data in motion is data that is transferred from one device to another across a network. Finally, data in use is when data is actively being accessed and processed by users and can be the most vulnerable state. It’s essential to ensure your data remains secure throughout its life cycle and that you’re taking all necessary precautions to protect it.
