Azure Intrusion Detection System (IDS) is an important part of a comprehensive security strategy for any organization. Azure IDS solutions allow organizations to detect, alert and respond to malicious activity on their networks in real time. This can help protect against unauthorized access, malicious code, and data breaches.
IDS solutions are divided into four main categories- network intrusion detection systems (NIDS), host-based intrusion detection systems (HIDS), perimeter intrusion detection systems (PIDS), and virtual machine-based intrusion detection systems (VMIDS). Each of these types has its own advantages and characteristics that make it suitable for certain environments or scenarios.
Network Intrusion Detection Systems (NIDS) are designed to monitor all traffic from the Internet or other external sources. They analyze the packets entering and leaving a network for signatures that match known attacks, as well as other suspicious activity such as port scans or denial of service attempts. NIDS can also detect anomalies in traffic behavior and alert administrators when something appears out of the ordinary.
Host-Based Intrusion Detection Systems (HIDS) are installed directly onto individual computers within a network. They monitor activities at the host level, such as system calls, log files, and configuration changes. HIDS can detect malicious software attempting to run on a computer, as well as unauthorized access attempts or changes in system settings that could indicate an attack is underway.
Perimeter Intrusion Detection Systems (PIDS) are designed to monitor traffic coming into a network from public sources such as the Internet or other external networks such as wireless connections. These systems analyze incoming traffic for signs of malicious activity such as IP address spoofing or port scanning attempts. PIDS also alerts administrators if incoming traffic exceeds predetermined thresholds or if there is an unusual spike in traffic from a particular source.
Finally, Virtual Machine-Based Intrusion Detection Systems (VMIDS) are specialized IDS solutions designed to protect virtualized environments such as cloud computing platforms or private data centers. VMIDS use heuristics to identify malicious activities on virtual machines by analyzing system calls, memory dumps, and application logs in order to detect potential threats before they cause any damage.
Azure IDS solutions provide organizations with comprehensive protection against malicious intrusions by monitoring all types of network traffic and detecting suspicious activities quickly and accurately. These solutions can help protect businesses against unauthorized access, malware outbreaks, and data breaches while providing real-time alerts so that administrators can take immediate action when threats are detected. The ability to detect threats quickly and respond effectively is essential for ensuring the security of any organization’s IT infrastructure today.
Understanding Intrusion Detection Systems (IDS) in Azure
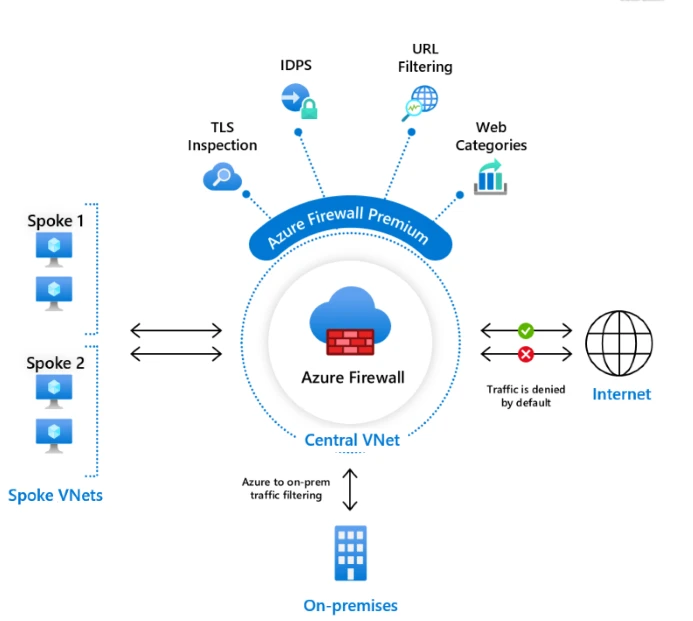
Azure Intrusion Detection System (IDS) is an advanced security service that monitors your Azure environment and detects malicious or unauthorized activities. It provides automated responses to any suspicious activity detected on the network, alerting administrators to take action quickly. Azure IDS uses a variety of techniques and technologies to detect malicious or suspicious activities, such as deep packet inspection, protocol analysis, signature-based detection, anomaly detection, and more. With this service, you can identify threats in real time before they become a problem. Additionally, it integrates with other Azure security services such as Security Center and Network Watcher to provide added visibility into your environment. With Azure IDS, you can quickly identify and respond to threats while protecting your data from potential malicious attacks.
Types of Intrusion Detection Systems
The four types of Intrusion Detection Systems (IDS) are Network Intrusion Detection Systems (NIDS), Host-Based Intrusion Detection Systems (HIDS), Perimeter Intrusion Detection Systems (PIDS), and Virtual Machine-Based Intrusion Detection Systems (VMIDS).
Network Intrusion Detection Systems are designed to monitor and detect malicious activities on a computer network. They use signature and anomaly-based detection methods to analyze the incoming packets and identify any suspicious activities that may be occurring. The advantage of using NIDS is that it can detect malicious traffic before it enters the network, reducing the chances of a successful attack.
Host-Based Intrusion Detection Systems are designed to monitor and detect malicious activities on single computer systems or devices. These systems rely on signature-based detection in order to identify any known attack patterns, as well as anomaly-based detection to identify new or previously unknown attacks. The advantage of using HIDS is that it provides additional security for individual hosts or devices in a networked system.
Perimeter Intrusion Detection Systems are designed to detect unauthorized access attempts at the perimeter level of an organization’s network infrastructure. These systems use both signature-based and behavior-based detection methods to analyze incoming traffic and identify any suspicious activity. The advantage of using PIDS is that it can help protect against external threats before they have a chance to penetrate the internal network.
Finally, Virtual Machine-Based Intrusion Detection Systems are designed specifically for virtual environments such as cloud computing platforms or virtual private networks (VPNs). These systems use both signature-based and anomaly-based detection methods in order to detect suspicious activities within these virtual environments. The advantage of using VMIDS is that it can provide additional security for applications running in these virtualized environments, allowing organizations to better secure their cloud applications and data against potential threats.
The Purpose of an Intrusion Detection System
The purpose of an Intrusion Detection System (IDS) is to detect malicious activities, such as unauthorized access attempts, malicious network traffic, and suspicious system changes. It works by monitoring the traffic on a network or host and analyzing it for any suspicious or malicious activity. The IDS can alert the security operations center (SOC) in real time when potential threats are detected. This allows the SOC analyst or incident responder to take action quickly to mitigate the threat and protect the system from further damage. Additionally, an IDS can also be used for forensic analysis of past incidents, helping organizations understand how a threat was able to gain access and what actions need to be taken in order to prevent future attacks.
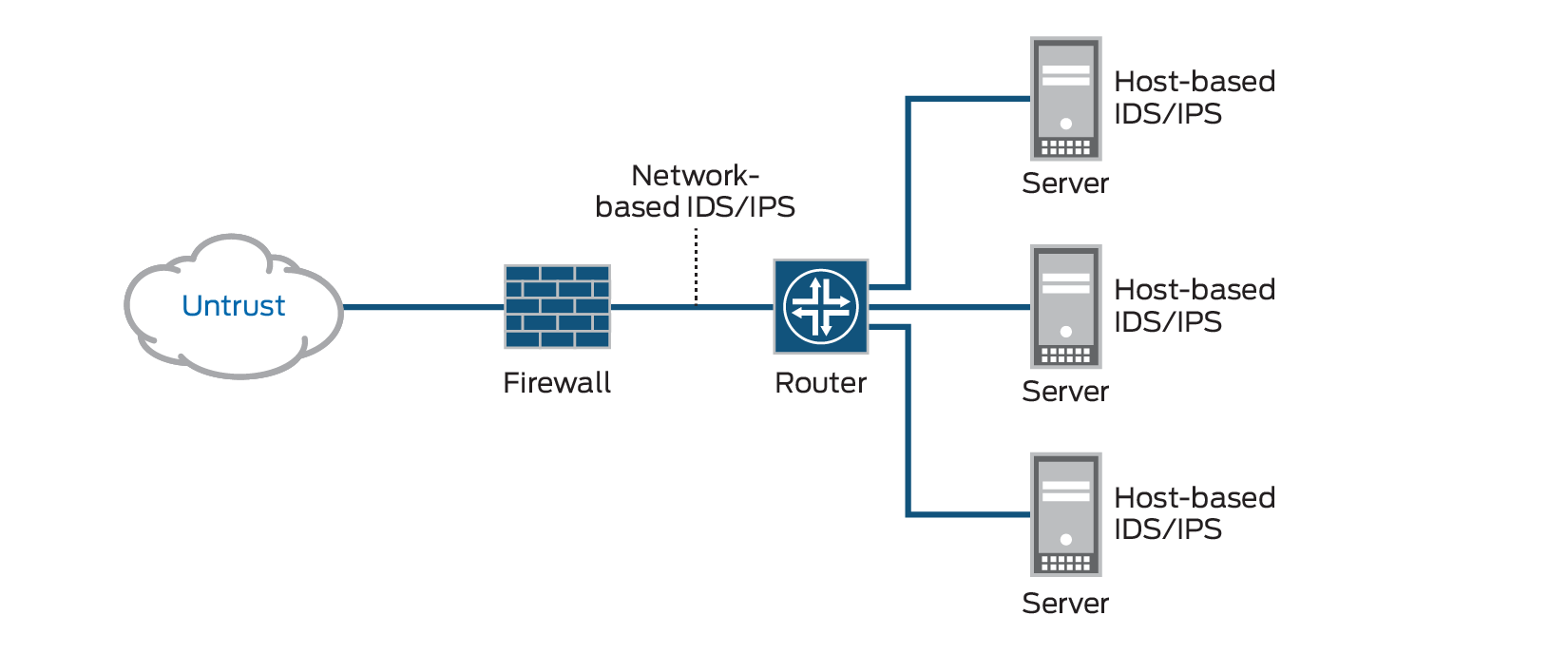
Components of an Intrusion Detection System
1. Network Intrusion Detection System (NIDS): This component monitors the incoming/outgoing traffic of a network and looks for suspicious activities, such as unauthorized access attempts or malicious code.
2. Host Intrusion Detection System (HIDS): This component monitors the activity on individual computer systems, such as user logins, file modifications, and application usage.
3. Audit Data Processor: This component collects audit data from various sources such as NIDS, HIDS, system logs, and packet capture devices, and converts it into a format that can be analyzed by other components of the IDS.
4. Knowledge Base: This component contains information about known attacks, their signatures, and other relevant information that is used to detect suspicious activity in network traffic or system activity.
5. Decision Engine: After analyzing the audit data collected by the Audit Data Processor, this component makes a decision whether an attack is taking place or not and sends an alarm to alert administrators if necessary.
6. Alarm Generation & Response: This component generates alert notifications to administrators based on the decisions made by the Decision Engine and also provides response mechanisms for administrators to take action against detected attacks.
Examples of Intrusion Detection Systems
Intrusion Detection Software (IDS) is a type of security software that is used to detect suspicious activities and potential threats on a computer or network. Examples of IDS include:
1. ManageEngine EventLog Analyzer: This is a real-time log monitoring and log management solution that offers file integrity monitoring and policy compliance. It also provides detailed reports, alerting capabilities, and data analytics for security analysis.
2. Snort: This open-source Network Intrusion Detection System (NIDS) monitors the network for malicious traffic, threats, and other suspicious activities. It can detect malicious packets as well as port scans, buffer overflows, web application attacks, SQL injections, and more.
3. OSSEC: This Host Intrusion Detection System (HIDS) provides file integrity monitoring, log analysis, rootkit detection, real-time alerting, and active response to mitigate threats in real-time.
4. CrowdStrike Falcon: This HIDS uses machine learning algorithms to detect threats before they can cause damage to your system or network. It also provides detailed forensic information about the attack vector used by an attacker so you can take preventive action quickly.
The Difference Between Active and Passive Intrusion Detection Systems
Active IDS is an intrusion detection system that actively takes action in response to an attack. It typically involves blocking the attack by configuring a firewall to block the source of the attack, or by stopping a malicious application or process. Active IDS can also be used to quarantine compromised systems and take steps to prevent future attacks.
Passive IDS, on the other hand, does not take any action in response to an attack; it only monitors and detects threats. It typically involves logging events, monitoring traffic patterns, and alerting personnel when suspicious activity is detected. By doing so, passive IDS can help organizations identify potential vulnerabilities and respond proactively to mitigate risk.
Differences Between IDS and Firewall
The primary difference between an Intrusion Detection System (IDS) and a Firewall is the purpose of each system. An IDS is designed to detect malicious activity on a network, while a firewall is designed to protect a network from malicious activity.
An IDS typically works by analyzing traffic on the network and looking for suspicious patterns or behavior. It can also detect unusual changes in system configurations, as well as activities that could indicate malicious behavior, such as port scans and attempts at unauthorized access. When it detects something suspicious, it will alert IT personnel or other stakeholders so they can take appropriate action.
A firewall, on the other hand, is designed to prevent unwanted traffic from entering or leaving a network. It does this by blocking access from known suspicious IP addresses or entities, or by checking incoming traffic against a set of rules that determine which traffic should be allowed and which should be blocked. A firewall can also be used to limit access to certain applications or services within the network.
In summary, an IDS monitors a network for potential attacks while a firewall blocks connections from known malicious sources. Both systems are important parts of any comprehensive security strategy and work together to ensure that the network remains secure.
Understanding Intrusion Detection Systems in Cloud Computing
Cloud IDS (Intrusion Detection System) is a security solution that monitors cloud-based resources and networks for malicious activities, such as unauthorized access attempts, malicious traffic, and hostile applications. Cloud IDS systems constantly watch over the cloud infrastructure looking for indications of potential attacks or suspicious activity. When triggered, they generate an alert to notify administrators of a potential attack or breach. Cloud IDS solutions can also provide full visibility into network activity by tracking changes to the data stored in the cloud and analyzing traffic patterns so that it can detect anomalies or unusual activity. This allows organizations to take proactive steps to protect their networks from cyber threats and maintain compliance with regulatory requirements.
The Benefits of Using Intrusion Detection Systems Over Intrusion Prevention Systems
IDS systems are an important part of any network security strategy because they provide a baseline for what kind of traffic is normal and which types of traffic might be malicious. By monitoring the traffic on a network, IDS systems can detect suspicious behavior, alert administrators, and provide data to help investigate potential threats. In comparison, an IPS system is designed to actively prevent malicious traffic from entering the network by blocking it or redirecting it away from critical resources.
While IPS can be effective in stopping attacks before they start, an IDS system provides additional value by helping to identify previously unknown threats and providing administrators with valuable data for further investigation. Additionally, IDS systems can also be used to monitor user activity on the network so that administrators can identify any suspicious behavior. By combining both IPS and IDS systems within a comprehensive security framework, organizations can ensure that their networks are better protected against both known and unknown threats.
Understanding IDS and IPS in Azure
IDS/IPS in Azure is a set of security tools designed to detect and protect against malicious activity on the Azure cloud platform. IDS stands for Intrusion Detection System, which is a system that monitors your cloud environment for malicious activities. It looks for suspicious activities such as unauthorized access attempts, system changes, or malware infections. It also has the ability to alert you when these types of events occur. IPS stands for Intrusion Prevention System, which is a system that blocks malicious activity from occurring in your cloud environment. It can prevent suspicious activities from taking place by blocking them before they happen. Both of these systems work together to provide comprehensive protection against potential threats to your Azure cloud environment. Additionally, you can use Azure Firewall threat intelligence-based filtering to further enhance your security posture by identifying and blocking traffic originating from known malicious IP addresses and domains sourced from the Microsoft Threat Intelligence feed.
The Necessity of Having Both Intrusion Detection Systems and Intrusion Prevention Systems
Yes, it is highly recommended that both an Intrusion Detection System (IDS) and an Intrusion Prevention System (IPS) be deployed together to provide the most comprehensive security coverage. An IDS can detect malicious activity on your network and alert you to potential threats, while an IPS actively blocks malicious traffic from entering your network. By deploying both solutions, you will be better equipped to protect your assets and servers from cyberattacks. With an IDS, you can monitor for suspicious behavior or patterns and gain insight into the source of any potential attack. And with an IPS, you can prevent any malicious traffic from entering your network in the first place.
Conclusion
In conclusion, Azure Intrusion Detection System (IDS) solutions and services are designed to detect and protect against malicious threats in the cloud. These solutions detect intrusions using three different methods: signature-based, anomaly-based, and hybrid intrusion detection. They provide an alert about potential incidents which enables a security operations center analyst to investigate the event and take necessary action. Furthermore, these solutions can also be used to block attempted intrusions or otherwise remediate the incident. Ultimately, Azure IDS is an invaluable tool for ensuring cloud security.