If you’re looking for a way to enable monitor mode on wireless interfaces, then airmon-ng is the perfect tool to do so. Airmon-ng is a command-line utility that comes with the Aircrack-ng package and it’s available for Linux/FreeBSD systems. It’s an incredibly powerful tool that can enable monitor mode on wireless interfaces, kill programs that interfere with the wireless card operation, and switch back from Monitor mode to Managed Mode.
When using airmon-ng, first use the command without any parameters to view the status of your wireless interfaces. You can then use airmen-ng to put one of your wireless interfaces into monitor mode using the following command:
airmon-ng start
Once you have enabled monitor mode on your interface, you can use airodump-ng to collect WEP IVs (Initialization Vector) or WPA handshakes. This is useful for cracking passwords with aircrack-ng. However, if you need to switch back to Managed Mode from Monitor Mode, you can use airmon-ng again:
airmon-ng stop
Remember that Windows only supports a limited subset of these commands, so if you’re running Windows make sure you check out the troubleshooting tips specific to XP and Vista before using airmon-ng.
Overall, if you need a powerful tool for enabling monitor mode on wireless interfaces then look no further than airmon-ng!
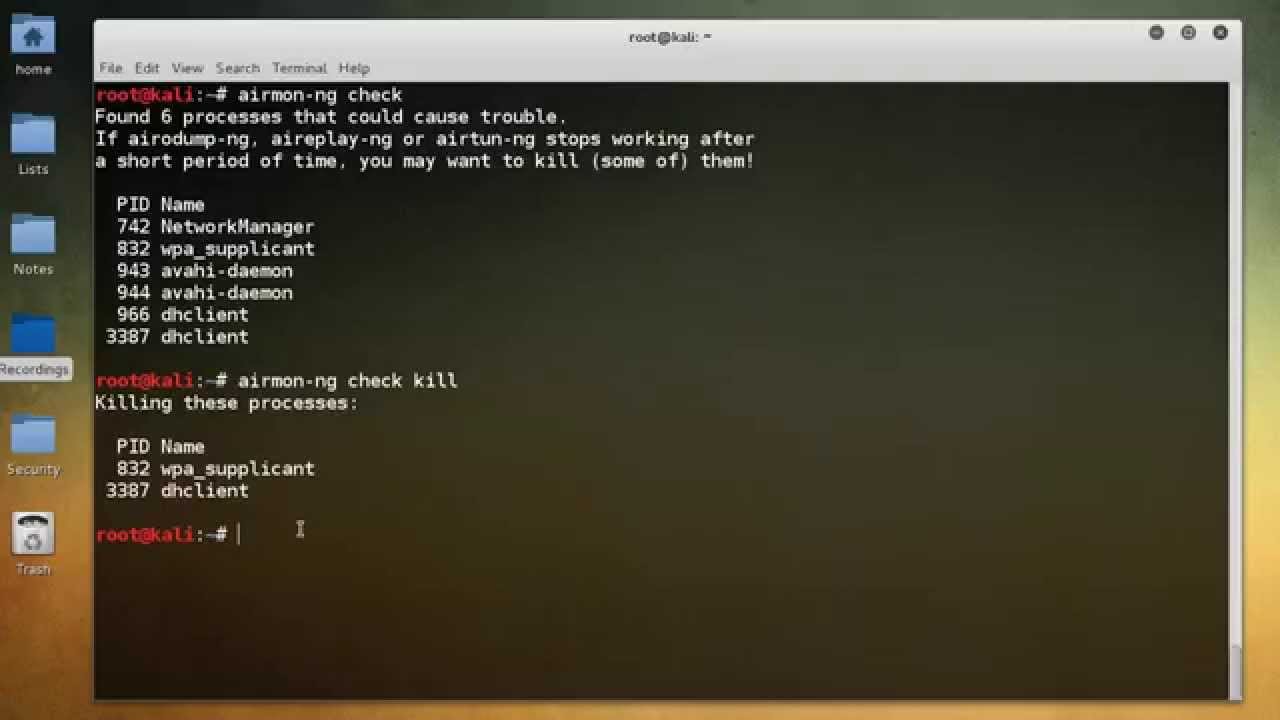
The Use of Airmon-Ng
Airmon-Ng is a script used to enable monitor mode on wireless interfaces. Monitor mode allows the user to capture and analyze all packets sent over a wireless network. It can be used to detect security vulnerabilities, such as weak encryption or unauthorized access points, as well as capture data for packet analysis. Airmon-Ng can also be used to switch an interface from monitor mode back to managed mode, and list or kill programs that interfere with the wireless card operation.
Using Airmon-Ng on Kali Linux
Airmon-ng is a powerful command-line tool included in the Aircrack-ng suite. It is typically used to enable monitor mode on wireless interfaces on Kali Linux, allowing users to monitor and capture traffic from wireless networks. Monitor mode allows users to passively listen to all traffic from a wireless network, including broadcast and multicast packets. In addition, Airmon-ng can also be used to switch back from Monitor mode to Managed Mode, allowing for normal operation of the wireless interface.
Understanding the Airodump-ng Command
The Airodump-ng command is a command line utility used in conjunction with a wireless network interface controller. It provides the ability to capture 802.11 frames and can be used to capture WEP IVs (Initialization Vectors) or WPA/WPA2 handshakes for use with aircrack-ng. The command is typically used in a terminal window, and can take the form of either:
• Airodump-ng [interface]
• Airodump-ng [interface] –bssid [BSSID] –channel [channel] –write [file prefix]
The first command simply starts the utility on the specified interface, while the second allows you to specify a specific BSSID, channel, and output file to write the captured frames to.
Utilizing Aircrack-ng for Attack Purposes
Aircrack-ng is a powerful tool attackers use to crack WEP and WPA/WPA2-PSK keys, allowing them to gain access to data that would otherwise be inaccessible. It can be used to detect wireless networks and monitor the packets passing through them, allowing an attacker to identify weak points and potential areas of attack. Additionally, aircrack-ng provides an attacker with the ability to crack WEP and WPA/WPA2-PSK keys, which can be used to gain unauthorized access to a network or system. This makes it a valuable tool for anyone looking to compromise security systems or steal confidential data.
Understanding Airodump-Ng in Cyber Security
Airodump-ng is an essential tool in cyber security. It is a command line application used to monitor and analyze 802.11 wireless LANs. It can detect all wireless access points (APs) and their associated clients, as well as capture data packets being transmitted over the network. This information can be used for various purposes such as detecting unauthorized access points, finding open networks, or assessing network security. Airodump-ng can be used in conjunction with other tools like Aircrack-ng to hack into the APs and gain access to the network. It is an important part of any cyber security toolkit, and its use should be part of any penetration testing process.
Comparing Wireshark and Aircrack-ng
Wireshark is a network protocol analyzer used for capturing, analyzing, and troubleshooting traffic on a network. It’s used to identify and diagnose problems on the network, detect malicious activity, monitor user behavior, and much more. On the other hand, Aircrack-ng is an aggressive tool that enables users to gain access to wireless networks by cracking their encryption keys. It can also be used to test the security of a wireless network by attempting to crack its encryption keys. The main difference between Wireshark and Aircrack-ng is their purpose; Wireshark is mainly used for monitoring network activity while Aircrack-ng is used for gaining access to wireless networks.
Understanding How Aircrack Works
Aircrack-ng is an open-source wireless network security tool designed to assess the security of wireless networks by exposing weaknesses in security protocols. It focuses on two main areas: WEP and WPA/WPA2.
When it comes to breaking WEP, Aircrack-ng relies on statistical mathematical analysis to identify the correct encryption key. It begins by capturing packets from the target network, then looks for patterns among them, such as repeated IVs (Initialization Vector) and other information that can be used to calculate the key. Once the key is calculated, Aircrack-ng can decrypt the data from the packets and reveal the plaintext message inside.
Breaking WPA/WPA2 is a bit different. Here Aircrack-ng uses a brute force attack technique against known passwords in order to guess the correct one. This means it will try every single possible password combination until it finds one that matches the encrypted handshake file it has captured from the network. Once this starts happening successfully, Aircrack-ng will have broken into your network and will be able to access all its data.
Is Aircrack a Free Software?
Yes, Aircrack-ng is free and open source. It is released under the GNU General Public License (GPL) and is available for both commercial and non-commercial use. Aircrack-ng includes a variety of tools to help assess the security of your Wi-Fi network, such as packet sniffers, intrusion detection systems, and tools to crack WPA/WPA2 keys. It also includes tools to capture and analyze network traffic, detect rogue access points, and crack WEP keys. All these tools are available for download from the Aircrack-ng website.
Conclusion
In conclusion, airmon-ng is a powerful command-line tool that can be used to enable monitor mode on wireless interfaces and capture raw 802.11 frames. It is an essential part of the Aircrack-ng package and is available only for Linux/FreeBSD systems. It can also be used to switch back from Monitor mode to Managed Mode, but this requires special considerations on Windows systems. Overall, airmon-ng is an important tool for users who want to ensure secure wireless connections and collect WEP IVs or WPA handshakes for use with aircrack-ng.