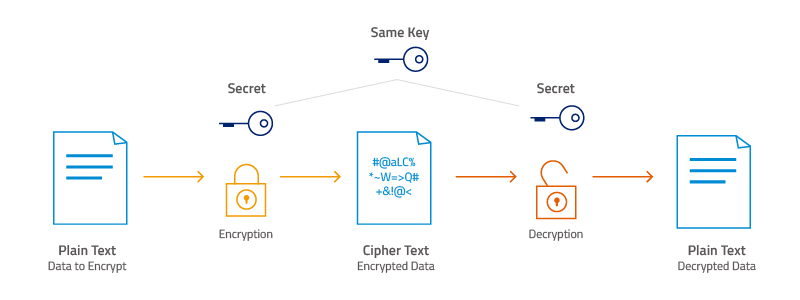
AES Encryption is an important and widely used form of data protection for governments, financial institutions, and other entities that need to keep their information secure. It is a block cipher algorithm that uses secret keys to encrypt data in order to protect it from unauthorized access. To understand how AES encryption works, let’s take a look at a simple example.
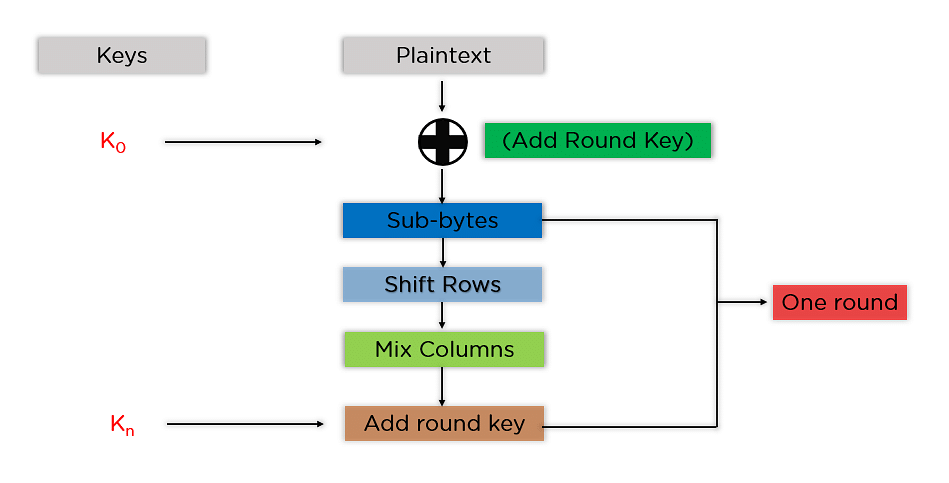
First, we need to divide the data into small blocks (generally 16 bytes). This is done so that each block can be encrypted separately using the same key. The next step is key expansion, where the key is expanded so it can be used for multiple rounds of encryption. After this, the round key is added to the starting state array, and nine rounds of state manipulation are performed. Each round involves byte substitution, shifting rows, mixing columns, and adding round keys.
The tenth and final round also involves byte substitution, shifting rows, and adding round keys; however, mixing columns isn’t necessary as this has already been done in previous rounds. After this final step, the encrypted data can then be safely transmitted over networks or stored in databases without fear of interception or tampering.
AES Encryption is an incredibly powerful tool for protecting sensitive information from prying eyes and malicious actors alike. It’s easy to see why it has become such an essential part of cybersecurity today – with its combination of speed, strength, and efficiency it remains one of the best ways to keep your digital assets safe from harm.
Uses of AES Encryption
AES encryption is used in a wide variety of applications to secure sensitive data. From government computer networks and military systems to banks and online retailers, AES encryption is an integral part of data security. It is also widely used for secure communication over the Internet, VPNs, file storage systems, and other applications. Additionally, many consumer devices such as smartphones and tablets utilize AES to keep your data safe from unwanted access.
AES encryption has become a widely accepted standard for protecting sensitive information due to its strong security features that have been tested and proven over time. It is also relatively efficient in terms of both time and resources required for implementation, making it an attractive choice for many organizations seeking to protect their data.
How to Perform AES Encryption
AES encryption is a type of block cipher encryption that can be used to protect data. It works by dividing the data into blocks, which are then encrypted using a key. The key is expanded using an algorithm and then each block is altered using a combination of substitution, shifting, and mixing columns. For each additional round of encryption, the round key is again added to the data until all the blocks have been encrypted. Once all the rounds are finished, the encrypted data is ready for transmission or storage.
The Current Use of AES Encryption
Yes, AES (Advanced Encryption Standard) is still in use today and remains one of the most secure and popular encryption algorithms available. AES is a symmetric-key encryption algorithm that was adopted by the National Institute of Standards and Technology (NIST) as a federal standard in 2001. It has since become the de facto standard for data encryption due to its high level of security, efficiency, and flexibility. AES is used to protect sensitive information such as credit card numbers, passwords, emails, web traffic, and other confidential data. It is also often used to protect data stored on hard drives or transmitted over networks and the internet. Government agencies, financial institutions, tech companies, and other organizations around the world rely on AES for protecting their confidential information. As technology continues to evolve and new challenges arise for security professionals, AES will remain a reliable form of encryption for years to come.
Step-by-Step Explanation of How AES Works
AES (Advanced Encryption Standard) is a symmetric-key encryption algorithm that is used to protect sensitive data. AES works by taking a plaintext message, which consists of an arbitrary amount of data, and transforming it into an unreadable ciphertext using a specific set of steps.
Step 1: The plaintext is divided into blocks of 128 bits (16 bytes).
Step 2: An initial round key, derived from a user-provided key, is added to the plaintext block.
Step 3: Nine rounds of substitution and permutation are applied to the state array. These include SubBytes, ShiftRows, MixColumns, and AddRoundKey transformations.
Step 4: The tenth and final round includes all the same transformations as the previous rounds except for MixColumns.
Step 5: The resulting ciphertext block is then outputted as an unreadable stream of characters.
In order to decrypt the ciphertext back into plaintext again, AES reverses all the steps listed above using the same key that was used for encryption in step 2.
Using AES in Real Life
AES is a widely used encryption standard that is used to secure data in many real-world applications. For example, AES encryption is used to secure online banking transactions and credit card information. It is also used to secure communications between two parties, such as instant messaging services like WhatsApp or email providers like Gmail. Additionally, it is the encryption standard of choice for many online services like Google Cloud Storage and Apple iCloud. On the hardware side, AES encryption can be found in hard drives, USB flash drives, and other forms of external storage devices. Finally, it is also often employed by companies to protect stored data on their internal networks as well as sensitive customer records and financial transactions.
Can AES Encryption Be Broken?
AES encryption is one of the most secure forms of encryption available today, and despite some popular belief and arguments, it has never been cracked. AES is designed to be resistant to brute force attacks, meaning that a computer would have to try a very large number of combinations in order to guess the correct key. This makes it virtually impossible to crack without knowing the key.
In modern cryptography, AES is used with keys that are 128 bits, 192 bits, or 256 bits in length. Although it is possible for a computer to guess these keys very quickly due to advances in processor speeds over time (known as Moore’s law), larger keys make this process much slower and more difficult. Thus, if an AES encryption key is large enough, it should be safe from being cracked by any modern computing technology.
Does Netflix Utilize AES Encryption?
Yes, Netflix does use AES. Netflix uses the Advanced Encryption Standard (AES) cipher in Galois/Counter Mode (GCM), which is available starting in TLS 1.2. This cipher is used to ensure secure data transmission between its servers and user devices. AES-GCM provides effective encryption that is more efficient than the alternative Cipher Block Chaining (CBC) method.
Does Bitcoin Utilize AES Encryption?
Yes, Bitcoin Core does use the Advanced Encryption Standard (AES) algorithm to secure its wallets. AES is a type of symmetric encryption algorithm which uses the same key for both encryption and decryption. It is considered one of the most secure algorithms available and has been used by the NSA to protect classified information. This means that when you create a wallet with Bitcoin Core, all of your data is securely encrypted with AES so that it cannot be accessed by anyone without the correct key.
When Is the Best Time to Use AES?
AES should be used whenever encryption is needed. This includes all situations where sensitive data needs to be protected from unauthorized access, such as confidential documents, financial records, personal information, and passwords. AES is also a popular choice for encrypting data sent over the internet, as it provides a high level of security while still being relatively fast and easy to use. Furthermore, due to its low computational requirements, AES can be used on consumer devices such as laptops and smartphones.
The Benefits of Using AES Encryption
AES is considered the best encryption because it provides strong cryptographic security that is both efficient and flexible. Its key length options (128, 192, and 256-bits) provide a range of security levels to suit different needs. AES is also designed to be resistant to brute-force attacks and other forms of cryptanalysis. Additionally, AES has been widely adopted by many organizations and is the de facto encryption standard for many industries. This makes it an attractive choice for protecting data as it is reliable and trusted by many organizations around the world.
The Four Main Functions of AES
1. Sub-Byte: A Sub-Byte is a non-linear substitution step used in AES. It operates on 8-bit bytes and substitutes each byte of the state with its corresponding entry from a fixed substitution table (S-box). This operation helps to make the encryption process more secure by making it harder to determine the input/output relationship between plaintext and ciphertext.
2. Shift Row: The shift row step involves shifting each row of the state matrix one, two, or three bytes to the left, depending on the row number. This operation helps maintain diffusion in the encryption process; meaning that any changes in input will cause large-scale changes in output.
3. Mix Column: The mix column operation is a linear transformation step that operates on each of the four columns of the state matrix independently by multiplying it with an invertible 4×4 matrix called MixColumnsMatrix. This operation helps increase confusion and further makes it difficult for an attacker to determine the relationship between plaintext and ciphertext.
4. Add Round Key: The add round key step is used to incorporate a round key derived from the cipher key into each round of the encryption process by adding it to each column of the state matrix using the XOR (Exclusive OR) function. This operation ensures that even if two plaintexts share some similarities, they will be encrypted differently due to different keys being used for their encryption process and hence increasing security against attackers.
Conclusion
In conclusion, AES encryption is an incredibly important form of security used all around the world to protect sensitive data. It works by dividing data into blocks, then performing key expansion, byte substitution, shifting rows, mixing columns, and adding round keys in sequence. These steps are repeated until the encryption is complete and the same process is used in reverse to decrypt the data. AES provides a reliable layer of protection against malicious actors attempting to access confidential information, making it an essential tool in the modern digital age.