Cerber ransomware is a sophisticated form of malicious software (malware) that infects computers, restricts access to files, and demands payment for their release. It’s become increasingly common in recent years, and it’s important to take steps to protect yourself from it.
This type of malware is typically spread through malicious attachments or links sent via email. It can also be installed on a computer if the user visits an infected website or downloads certain files from the internet. Once installed on a device, Cerber will encrypt various types of data files and then demand payment for their release. The attackers usually require payment in Bitcoin or another cryptocurrency for the decrypt key.
As with any form of ransomware, it’s important to take steps to prevent a Cerber infection in the first place. One of the best ways to do this is by educating users about the dangers of clicking on unknown emails or downloading suspicious files from the internet. Additionally, it’s essential to maintain strong antivirus software that can detect and block malicious threats before they can infect your system.
If you do find yourself infected with Cerber ransomware, there are several things you should keep in mind:
• Do not pay the ransom – while there is no guarantee that paying will lead to successful decryption, doing so only encourages cybercriminals and could put you at risk for further attacks.
• Disconnect from the network – this will prevent any additional encryption from taking place and limit the damage done by an infection.
• Use system restore – if you have a recent backup of your system available, use it to roll back your computer and undo any changes made by Cerber ransomware.
• Scan your system with antivirus – run a full scan of your computer using an up-to-date antivirus program in order to detect and remove any remaining traces of Cerber ransomware from your system.
• Try a decryptor tool – there are several tools available online that can help decrypt files encrypted by Cerber ransomware; however, success rates vary significantly depending on how new or old the virus is and whether or not it has been modified since its initial release.
Cerber ransomware is a serious threat that requires vigilance on behalf of users as well as organizations in order to keep computers safe. By following these tips and taking steps to educate users about cyber security best practices, you can greatly reduce your chances of becoming infected with this dangerous form of malware.

The Targets of Cerber Ransomware
Cerber ransomware targets endpoints, such as desktops and laptops. It does not typically target servers, but it can still infect them if proper security measures are not in place. Cerber is a type of ransomware that encrypts files on the targeted computer and demands payment for the decryption key. It is often distributed through malicious email attachments, exploit kits, or drive-by downloads. Once installed, Cerber scans the system to identify and encrypt files with certain extensions such as .docx, .jpg, etc., making them inaccessible until a ransom is paid. In some cases, it can also install other malware onto the infected computer.
Source: cloudflare.com
Decrypting Cerber Files
The first step to decrypting Cerber files is to not pay the ransom. This will only encourage the ransomware authors and do nothing to help you regain access to your data. Instead, you should disconnect or remove any infected parts from your network immediately and use a system restore to go back to a clean state. You can then scan your system with an antivirus program to make sure that all traces of the malware have been removed.
Once this is done, you can look into using Cerber decryptor software, which is designed specifically for the decryption of .cerber files. These tools may be able to recover the encryption key used by the ransomware and allow you to decrypt your files. However, it should be noted that these tools are not always successful in recovering the key, so there is no guarantee that they will work in all situations.
If these methods fail, then unfortunately it may not be possible for you to retrieve your data without paying the ransom. As such, it is important that you always keep regular backups of important files so that they can be restored if needed in such an event.
Understanding How CryptoLocker Ransomware Works
CryptoLocker ransomware is a type of malicious software (or “malware”) that is typically spread through email phishing campaigns. Once a computer is infected, the malware will encrypt files stored on the hard drive or any attached network drives. This encryption prevents access to the data unless a ransom is paid for a decryption key. CryptoLocker also creates and runs a process that replaces the user’s desktop wallpaper with instructions on how to pay the ransom. In addition, it may modify Windows registry entries to ensure that it runs when Windows starts up and may also disable certain programs such as anti-virus programs.
The primary goal of CryptoLocker ransomware is to extort money from victims by holding their important data hostage and forcing them to pay for its release. Victims are usually presented with a countdown timer and an amount they must pay in order to regain access to their files before time runs out. Payments are typically required in cryptocurrencies such as Bitcoin or Monero, and payments must be made within the allotted time frame or else the decryption key will be destroyed and access to the encrypted files will be lost forever.
Decrypting Ransomware: Is It Possible?
Yes, it is possible to decrypt files that have been encrypted by ransomware. Depending on the type of ransomware, there are a number of different tools and methods that can be used to recover encrypted files. For example, some ransomware may be decrypted using a tool that specifically targets that variant, while other ransomware may be decrypted using a combination of anti-malware software and manual recovery techniques.
In most cases, it is best to seek professional help if you want to successfully decrypt your files. Security experts can identify the type of ransomware and provide advice on how to decrypt the affected files. Additionally, they can also help prevent future attacks by providing guidance on how to secure your systems against future threats.
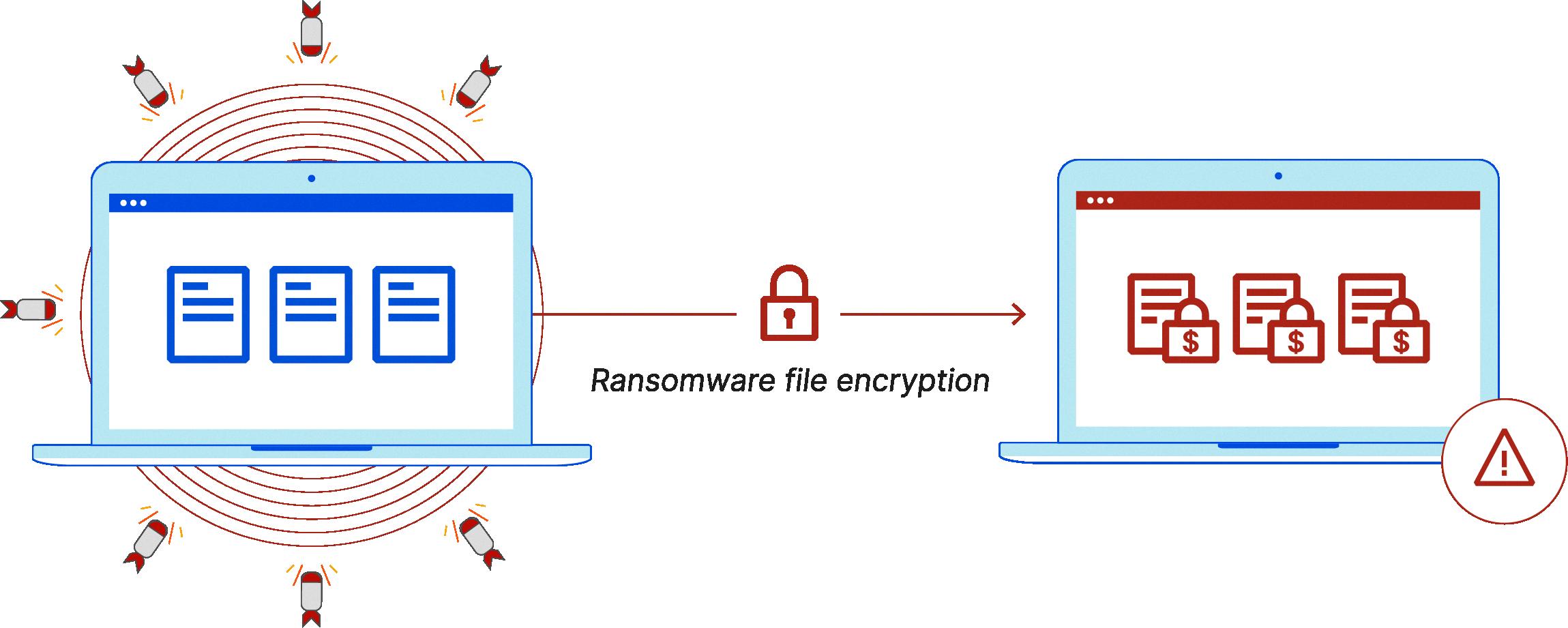
How Cerber Works
Cerber is a type of ransomware that encrypts the victim’s files, making them inaccessible until a ransom is paid. Once a computer is infected, Cerber begins to encrypt files on the hard drive as well as any connected external drives or network shares. It uses a combination of symmetric and asymmetric encryption algorithms to make it difficult to decrypt the data without the decryption key.
Once the encryption process is complete, Cerber displays an alert on the victim’s computer as their screensaver with instructions on how to pay the ransom. These instructions usually include payment details, such as a bitcoin address or other payment methods. The victim then has a set amount of time before the ransom amount increases or their files are deleted permanently.
To further complicate things for victims, Cerber also uses various methods to evade detection and spread itself across networks. It can be installed by malicious links in emails or websites, exploit vulnerabilities in software programs, and even use techniques like file-less malware which doesn’t require files to be stored on disk.
Once installed, Cerber can also delete system restore points and disable certain security features. This makes recovery from an infection more difficult without paying the ransom or using other data recovery tools.
Identifying Cerber as a Type of Malware
Cerber is a type of ransomware, a form of malicious software designed to encrypt files on a computer or device and then demand payment in order for them to be decrypted. It is usually spread by email attachments, malicious links, or drive-by downloads from malicious websites. Cerber uses strong encryption, and once the user’s files have been encrypted there is currently no free way to decrypt them. The ransomware uses a ransomware-as-a-service (RaaS) model where affiliates purchase and then subsequently spread the malware. Developers receive commissions for each copy used.
What is a Cerber File?
A Cerber file is a type of ransomware that encrypts your data and then demands a ransom payment in order for it to be decrypted and returned to you. It works by encrypting all your files, including documents, photos, videos, music, and other important files, with a strong encryption algorithm. Once the encryption is complete, the only way to access the encrypted data is by paying a ransom to the cybercriminals who have created and deployed this malicious software. Without paying the ransom, you will not be able to access your files again.
Does Factory Reset Remove Ransomware?
A factory reset can be an effective way to remove ransomware from your device. It will erase all the data, software, and settings from your device and reinstall a fresh version of the operating system. This will remove any malicious programs, including ransomware, as long as it does not have access to other parts of the system or to other networks. If a ransomware attack has only targeted certain file types, such as Office files, then a factory reset should eradicate those infected files and your machine will recover in a clean state.
Removing Ransomware Through Computer Wiping
Yes, wiping a computer can help remove ransomware from your system. Wiping a computer involves completely wiping the hard disks of all data and reinstalling everything from scratch. This ensures that no traces of malware remain on the system. Additionally, it is important to update your operating system and antivirus software regularly to help protect against future threats.
Conclusion
In conclusion, Cerber ransomware is a highly destructive form of malicious software that can lead to the encryption of your files and other data. It is important to take precautions to protect yourself from this type of attack, such as ensuring that you have up-to-date antivirus software installed, avoiding clicking on suspicious links or attachments, and backing up your data regularly. While it is possible to decrypt files infected with ransomware using specialized decryption tools, it is best to take preventative measures in order to avoid becoming a victim in the first place.








