Active Directory forests are an important part of the Microsoft Windows network infrastructure. An Active Directory forest is a logical container that contains domains, users, computers, and group policies. The forest is the highest level of organization within an Active Directory structure and provides a single global address list, a single database, and a security boundary. By default, users and administrators in one forest cannot access another forest.
For businesses that need to manage multiple domains, an Active Directory forest can be used to create an organized structure for managing the different domains. This structure can be used to restrict access between certain domains or enforce certain policies across all of them. Additionally, having a single global address list allows users on different domains to find each other easily and securely.
When setting up an Active Directory forest, there are several steps to consider:
1. Define the scope of your environment: what networks will be included in the forest and what type of resources will it contain?
2. Create a root domain: this is the first domain in your forest and it should have the same name as your organization’s DNS name (e.g., mycompany.com).
3. Create user accounts: create user accounts for each person who will need access to resources within the domain or across other domains within the forest; this includes administrators who will manage resources in all domains within the forest
4. Establish trust relationships between domains: establish trust relationships between all domains so that users can access resources from any domain within the network
5. Configure group policies: configure group policies that govern how users interact with resources on each domain; these policies can help you ensure that certain types of data are secure while allowing unrestricted access to other types of data
6. Monitor usage: monitor how people use resources on each domain so you can detect potential threats or misuse of sensitive information
7. Update regularly: update active directory forests regularly with new security patches and software updates to keep them secure
Having an organized Active Directory Forest in place helps businesses maintain secure networks for their employees and customers alike by providing them with tools for restricting access between different networks or enforcing certain policies across all of them, thus aiding organizations in their efforts towards better system security management practices overall.
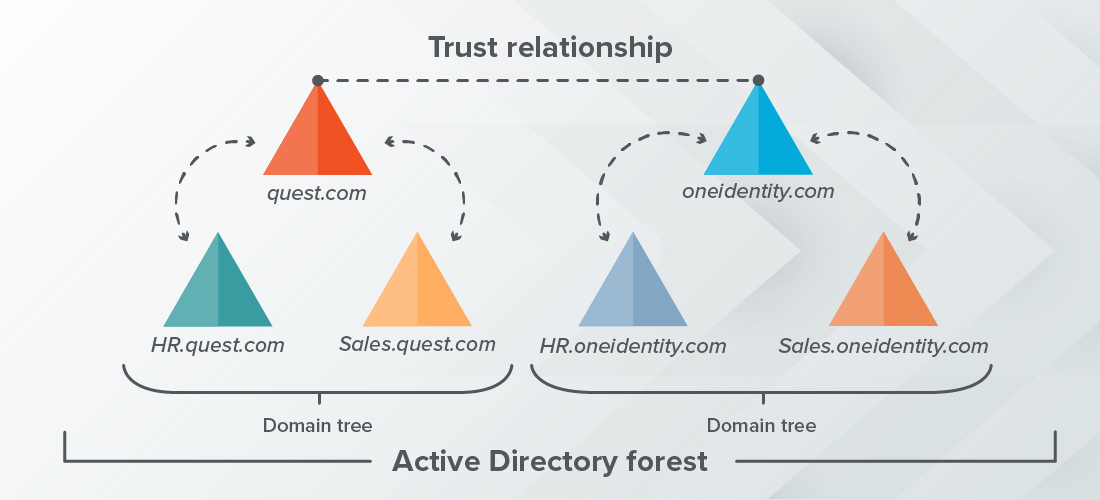
What is an Active Directory Forest and Tree?
Active Directory (AD) is a hierarchical directory service used by Windows servers to store information about network resources, such as users, computers, and printers. In an AD environment, each domain is represented by a tree structure, with each domain having its own parent domain or root domain. The forest is the overarching concept that encompasses all the domains in a single AD environment. A forest is essentially a collection of trees (domains) that are linked together and share a common schema.
A tree in an AD environment consists of one or more domains linked together in a hierarchical manner. The topmost domain in the tree structure is referred to as the root domain. All other domains beneath the root domain are known as child domains. Each child domain can contain its own set of user accounts, groups, computers, and other objects.
The forest provides additional functionality beyond what can be achieved with just one tree or one domain. It allows you to create trust relationships between different trees and domains within an environment. This enables resources from different AD trees and domains to be shared across the entire forest and simplifies administration tasks such as user account management across multiple locations or departments.
What is an Active Directory Forest and Domain?
An Active Directory forest is the highest level of organization within an Active Directory deployment. It contains all the domains, users, computers, and group policies for the network.
A domain is a logical grouping of objects that share a common directory database. Each domain in an AD forest has its own security settings, user accounts, and group policies. Domains are used to organize large networks into smaller administrative units, allowing administrators to manage resources more efficiently. A single user can be a member of multiple domains within the same AD forest.
By creating trust between domains, administrators can control access to resources across multiple domains and provide secure communication between them. Trusts also allow users from different domains to access each other’s resources without needing to log in separately. This helps make managing user accounts much easier and more secure than managing them separately in each domain.
Understanding the Difference Between Active Directory Domain, Tree, and Forest
Active Directory Domain: An Active Directory domain is a collection of objects within a Microsoft Active Directory network. The objects can include user accounts, computer accounts, organizational units, printers, applications, and other network resources. Every domain has a unique name and an associated security boundary.
Active Directory Tree: An Active Directory tree is a collection of domains within a Microsoft Active Directory network. Each domain in the tree has exactly one parent domain which leads to a hierarchical tree structure. All domains within the tree share the same namespace, which makes them easier to manage and identify.
Active Directory Forest: A group of AD trees is known as an Active Directory forest. A forest provides the highest level of trust between domains and allows administrators to manage multiple domains from a single location. It also helps to ensure that any changes made to one domain do not affect other domains in the forest.
Understanding the Active Directory Forest Level
Active Directory forest level is the highest level of organization within Active Directory. It is a logical entity that contains all of the objects, such as users, computers, groups, and other network resources, that are present in the directory. Each forest shares a single, unified database and a single global address list. It also provides a security boundary since users or administrators from one forest cannot access another forest by default. The forests are linked together to form a hierarchical structure so that there can be multiple domains and multiple forests in an organization. This enables organizations to manage different parts of their network independently while still maintaining centralized control over resources.
The Four Parts of Active Directory
The four parts of an Active Directory are Forests, Trees, Domains, and Organizational Units (OUs).
A forest is the highest level of organization in Active Directory. It consists of one or more trees and contains all objects in the directory. A tree is a hierarchical structure within a forest that consists of one or more domains that share common characteristics. Domains are the second level in the hierarchy, providing a secure boundary for user accounts and other objects. Within each domain is an OU structure that allows you to organize objects such as users, computers, groups, and printers into logical containers. Finally, Global Catalogs provide an index of all objects within a forest and allow for fast searching across domains.

Source: yuenx.com
Types of Active Directory
An active Directory is a powerful tool used to manage users, computers, and other network resources within an organization. It provides a secure platform to store data and define permissions for accessing that data. Within Active Directory, there are two distinct types of groups: Security Groups and Distribution Groups.
Security Groups are used to assign permissions to shared resources such as printers and files. These groups can be configured so that only certain members have access to certain resources. Security Groups can also be nested, meaning that one group can be assigned permissions on behalf of another group, allowing effective control and management of user access rights.
Distribution Groups are mainly used to create email distribution lists. They are typically used by organizations that need to send the same message or information out to multiple users at once, without having to type in each individual user’s name. Distribution Groups can also be used for other purposes such as allowing specific sets of users to access common files or applications.
By using Security and Distribution Groups within Active Directory, administrators are able to effectively manage user access rights across their organization’s network in a secure and efficient manner.
Number of Forests in Active Directory
The number of forests in an Active Directory environment can vary depending on the organization’s needs. Generally speaking, organizations that have multiple business units or other distinct groups may need more than one Active Directory forest in order to properly administer access control, security policies, and other resources. It is also possible for organizations to use a combination of the three main AD forest design models (organizational, resource, and restricted access) to create a hybrid forest structure that meets their specific needs. Ultimately, the number of forests within an Active Directory environment will depend on the unique requirements of each organization.
Types of Forests in Active Directory
Active Directory offers two types of forests for organizing resources and services within an organization: the organizational forest model and the resource forest model.
The organizational forest model is the traditional approach to Active Directory, where a single forest contains all of the objects—such as users, computers, and security groups—and also provides global authorization across multiple domains. The resource forest model is a newer approach that separates user accounts from other objects, such as computer accounts, security groups, and applications. This allows organizations to create separate forests for different types of objects so that they can be managed more securely.
Creating a Forest in Active Directory
Creating a forest in Active Directory is an important step in setting up a Windows Server environment. To begin, you must first install the Windows Server OS on a virtual machine and configure it with the necessary roles and settings, such as changing the hostname and assigning an IP address. Once this is complete, you must promote the server to a domain controller. To do this, open Server Manager, select Add Roles and Features, then select Active Directory Domain Services. After clicking through the prompts, you will be asked to add a new forest. Enter your desired forest name and click OK. Now reboot your server to apply the changes. Finally, you can use the command line to further configure your new forest.
Basic Active Directory Roles
The three basic Active Directory roles are Domain Controller, Global Catalog, and Operations Master.
A Domain Controller is a server that runs the Active Directory domain services. It stores all the user accounts, computer accounts, group policies, and other information related to the domain. It is also responsible for the authentication and authorization of users who log in to the domain.
The Global Catalog role is a distributed database that contains a partial replica of all objects from every domain in a multi-domain forest. It stores information such as user names, groups, computers, organizational units, and other directory objects. The Global Catalog allows users to quickly search and find information across multiple domains in an Active Directory forest.
The Operations Master role is responsible for managing certain operations within a domain or forest such as assigning security IDs (SIDs) to objects, removing objects from the directory, creating new trusts between domains, and updating group policy settings. The Operations Master is also known as Flexible Single Master Operation (FSMO) role.
Components of an Active Directory
Active Directory (AD) is a Windows-based directory service that provides authentication, authorization, and management of resources in a distributed network environment. It is the backbone of the Microsoft Windows server infrastructure and provides the foundation for secure access to network resources.
The three main components of an Active Directory are domains, trees, and forests.
A domain is the primary security boundary for an AD network. It is a logical grouping of users, computers, printers, and other objects that share a common set of security policies and trust relationships with one another. Domains are typically organized into hierarchical structures based on their purpose or geographic location.
A tree is a collection of one or more domains that have a contiguous namespace structure. All domains in a tree share the same schema and global catalogs, as well as trust relationships with each other. Trees can be further divided into sub-trees with different namespaces if needed.
A forest is a collection of trees that have transitive trust relationships between them. This allows users in one tree to access resources in another tree without needing to authenticate again. Forests provide an additional layer of security by allowing administrators to delegate administrative control of different parts of the directory to different teams or departments within the organization.
Conclusion
In conclusion, an Active Directory Forest (AD Forest) is a collection of trees within an Active Directory configuration that contains domains, users, computers, and group policies. It is the highest level of organization within the Active Directory and provides a single database, global address list, and security boundary for all trees in the forest. By default, users from one forest cannot access another forest. This feature allows for secure segregation between corporate resources and provides efficient management of user accounts and other entities across multiple forests.